
by Ciright | Jan 23, 2026 | Blogs
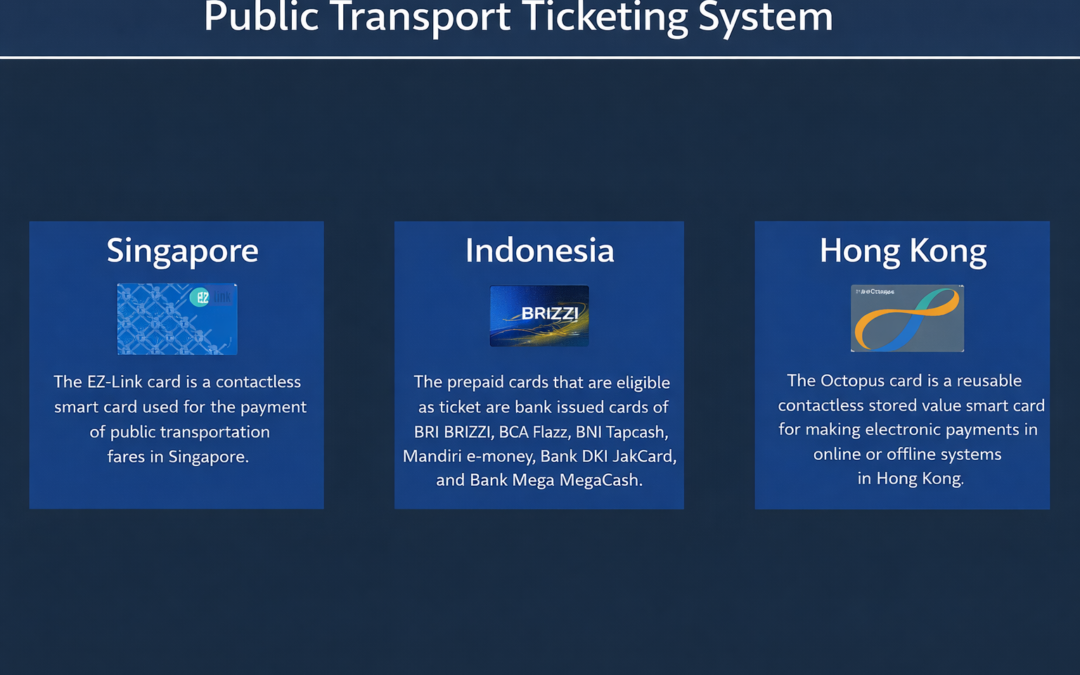
Dear Reader, This post is a follow-up post from our earlier post on Public Transport Ticketing System posted last week. If you have not read that we urge you to click here and view it before continuing to read this blog. This is our attempt to analyze the...

by Ciright | Jan 23, 2026 | Blogs
Dear Readers, Today the world is picking up any solution that can help fight COVID-19 and unfortunately, this situation has given birth to rampant myths and misunderstandings against technologies that can save you and your loved ones against this pandemic. As a...

by Ciright | Jan 23, 2026 | Blogs
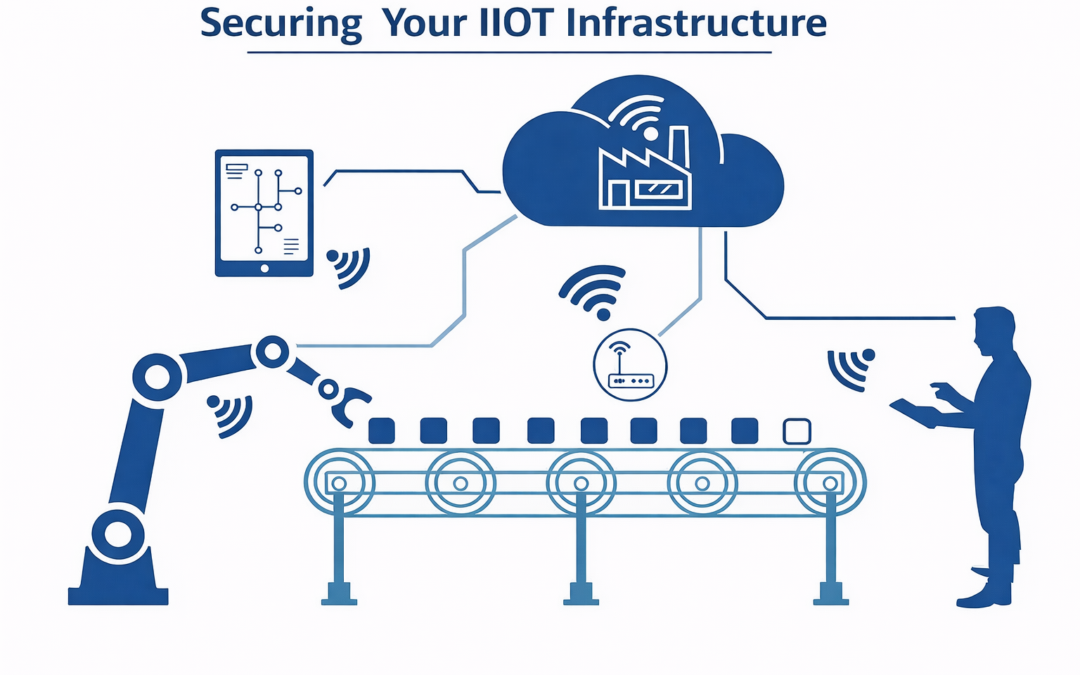
Dear Reader, Today, IoT devices have a deeper penetration in manufacturing, healthcare, and business than in our homes or phones; you can expect that trend to continue. For companies interested in implementing an industrial Internet of Things system, this article will...

by Ciright | Jan 23, 2026 | Blogs
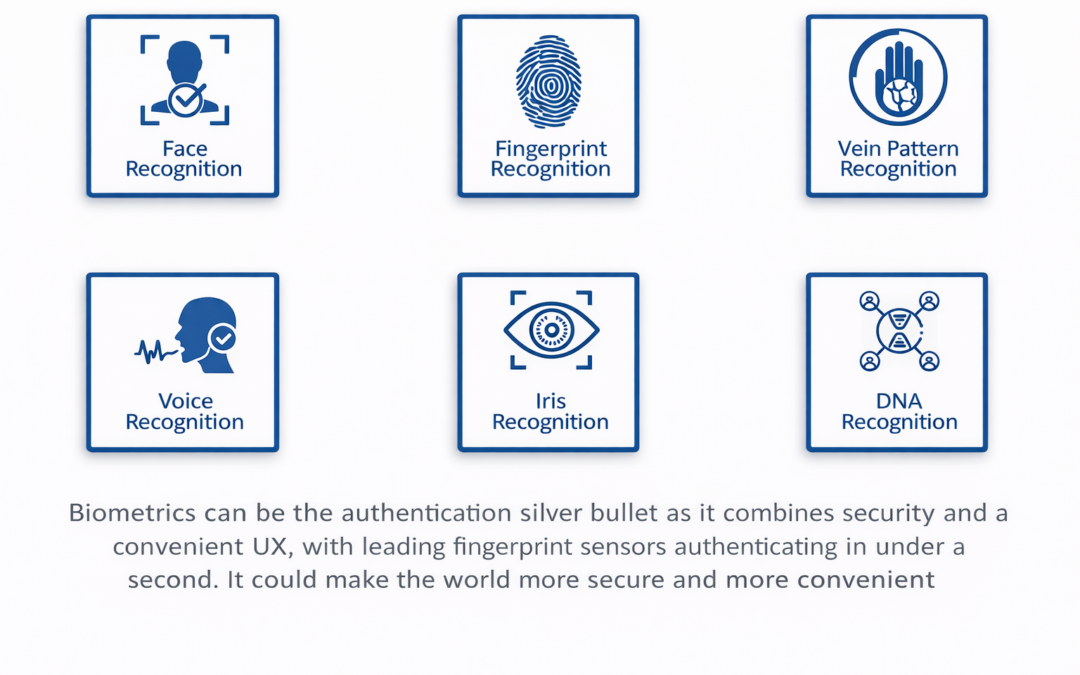
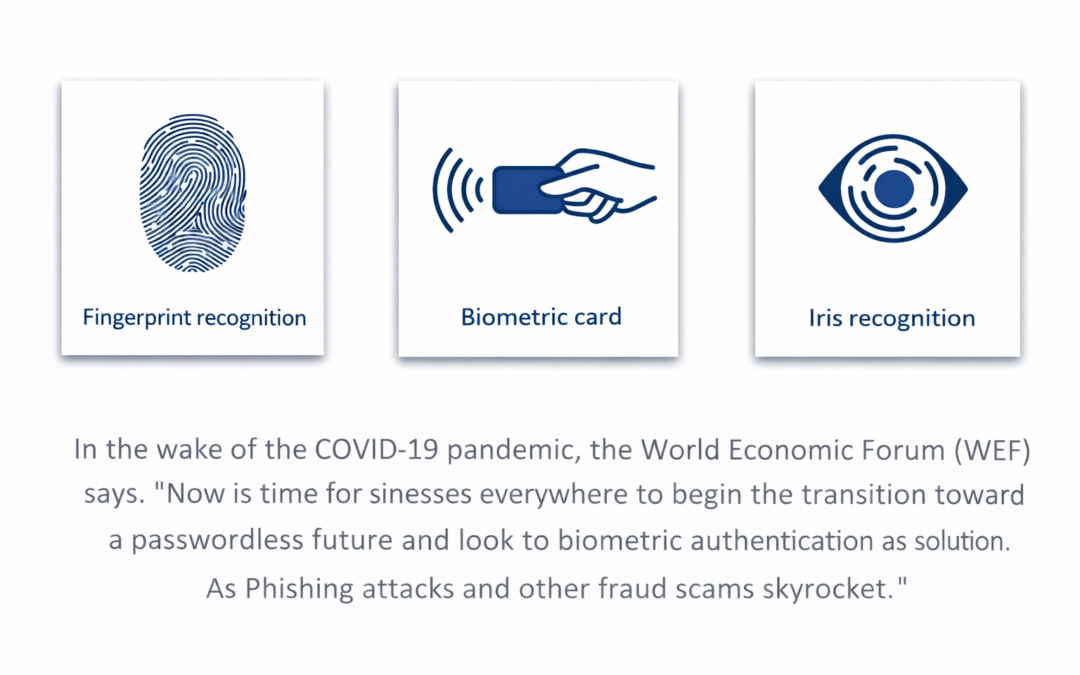
Dear Reader, We have tried to analyze how organizations can use biometrics technologies and protect individuals’ privacy in the journey to high performance. Ambimat Electronics with its experience of over 4 decades as an ODM of IoT products wishes to draw the...

by Ciright | Jan 23, 2026 | Blogs
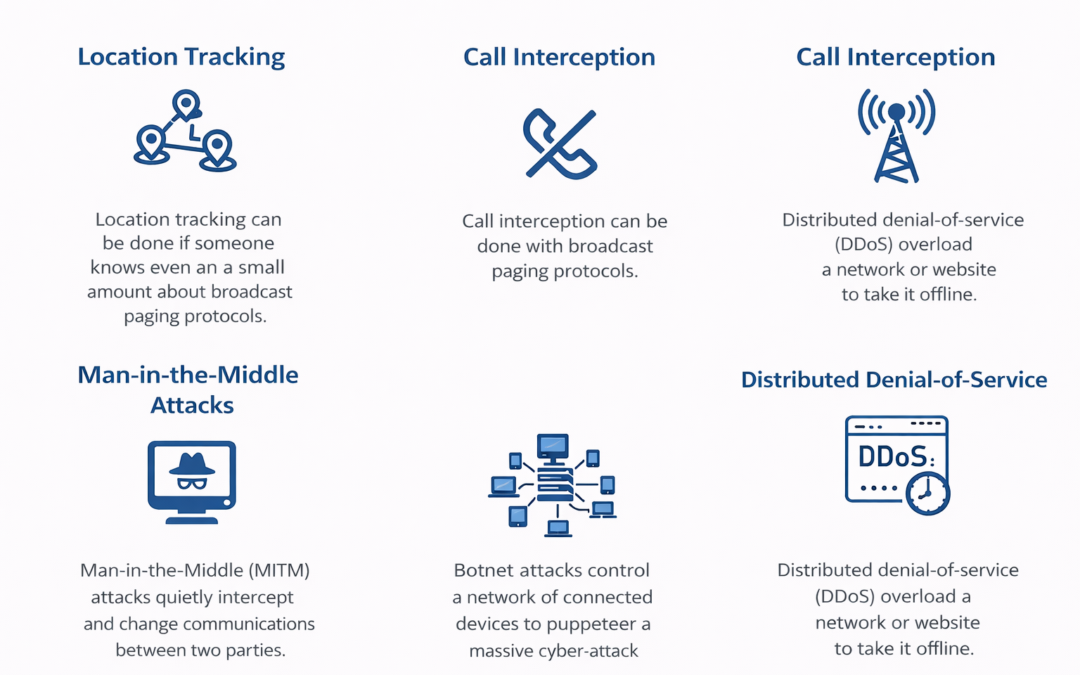
Dear Readers, This week’s blog is How secure is 5G? Developing technologies like the Internet of Things (IoT) is expected to grow with 5G. However, hackers are already targeting their vulnerabilities as new windows for widespread cyber-attacks. Better cybersecurity is...

by Ciright | Jan 23, 2026 | Blogs
Dear Readers, This week’s blog tries to examine; Biometrics can secure a wide range of devices and access points, from laptops and applications to access pads and key fobs. And in combination with existing authentication solutions, biometrics offer the possibility to...



Recent Comments