Tech Talk
Non Cellular Network based Wide Area Networks
Dear Reader,
This blog is a follow up from our earlier blog introducing LPWANs and their types. If you have not seen that article we urge you to visit the article by clicking here
As previously discussed there are a two of the most popular Non Cellular Network based WANs
– Sigfox
– LoRa and LoRaWAN
Sigfox:
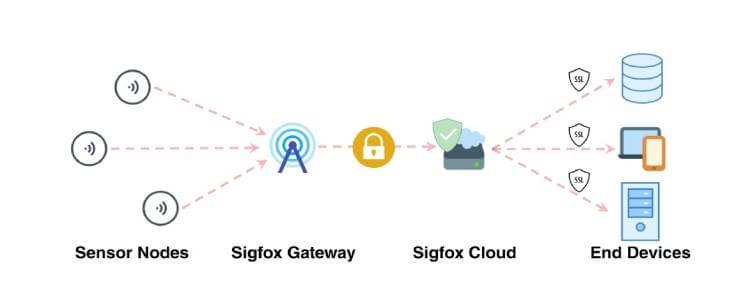
Sigfox is a French company founded in 2009 that builds wireless networks to connect low-power objects such as electricity meters and smartwatches,; which need to be continuously on and emit small amounts of data.
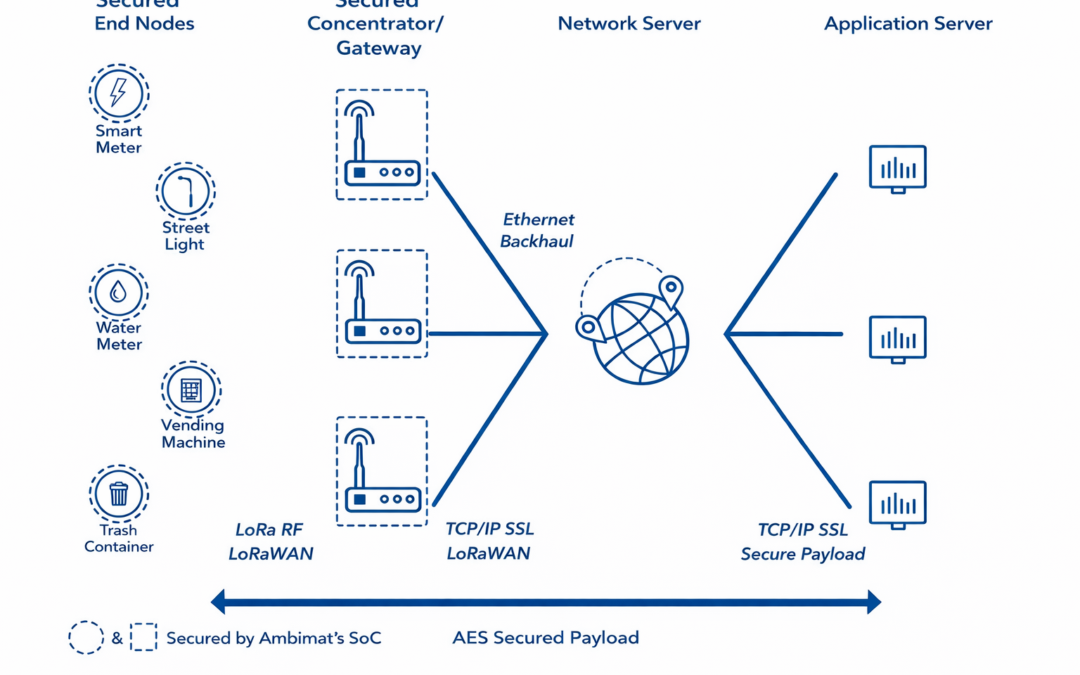
Sigfox employs a proprietary technology that enables communication using the Industrial, Scientific and Medical ISM radio band which uses 868MHz in Europe and 902MHz in the US. It utilizes a wide-reaching signal that passes freely through solid objects, called “ultra narrowband” and requires little energy, being termed “Low-power Wide-area network (LPWAN)”. The network is based on one-hop star topology and requires a mobile operator to carry the generated traffic. The signal can also be used to easily cover large areas and to reach underground objects.
It has partnered with a number of firms in the LPWAN industry such as Texas Instruments, Silicon Labs and ON Semiconductor. The ISM radio bands support limited bidirectional communication. The existing standard for Sigfox communications supports up to 140 uplink messages a day, each of which can carry a payload of 12 Bytes (excluding message header and transmission information) and up to 4 downlink messages per day, each of which can carry a payload of 8 Bytes.
LoRa and LoRaWAN
The LoRa Alliance is an open, non-profit association formed to foster an ecosystem for certain LPWAN technologies. It has about 400 member companies throughout North America, Europe, Africa, and Asia, and its founding members include IBM, MicroChip, Cisco, Semtech, Bouygues Telecom, Singtel, KPN, Swisscom, Fastnet, and Belgacom.
LoRaWAN is the open-standard networking layer governed by the LoRa Alliance. However, it’s not truly open since the underlying chip to implement a full LoRaWAN stack is only available via Semtech. Basically, LoRa is the physical layer: the chip. LoRaWAN is the MAC layer: the software that is put on the chip, to enable networking.
Simply put LoRa has the range of your mobile phone with the flexibility of Bluetooth or WiFi and the battery life of your watch for the cost of a beer.
The functionality is similar to SigFox in that it’s primarily for uplink-only applications—data from sensors/devices to a gateway—with many end-points. Instead of using narrowband transmission, however, it distributes information across different frequency channels and data rates using encoded packets. These messages are less likely to collide and interfere with one another thereby increasing the capacity of the gateway.
The main characteristics of LoRaWAN are:
- Long range (>5 km urban, >10 km suburban, >80 km VLOS)
- Long battery life (>10 years)
- Low cost (<$5/module)
- Low data rate (0.3 bps – 50 kbp, typically ~10 kB/day)
- Secure (largely depends on the implementation)
- Operates in unlicensed spectrum
- Localisation support
- Bidirectional
As you can see in the list of characteristics, everything sounds outstanding except when we’re looking at the data rate and security. Unfortunately, physically limited, wireless communication is always a trade off between distance, speed and power (energy). LoRa was designed with use cases in mind where this data rate should be enough and the other characteristics are way more important. Security in most cases is considered a relative term. One technology is more secure than the other and the concept of a 100% secure solution is, unfortunately, still a myth.
LoRaWAN was also designed with large service providers in mind. Just as with the cellphone network: a few operators that maintain and control the network and millions of users that exploit the network and do not need to care about the infrastructure. Nevertheless, since LoRa is operating in unlicensed spectrum, it’s perfectly possible to set up your own gateway(s), have a coverage of a few kilometers and run your own network.
Use cases
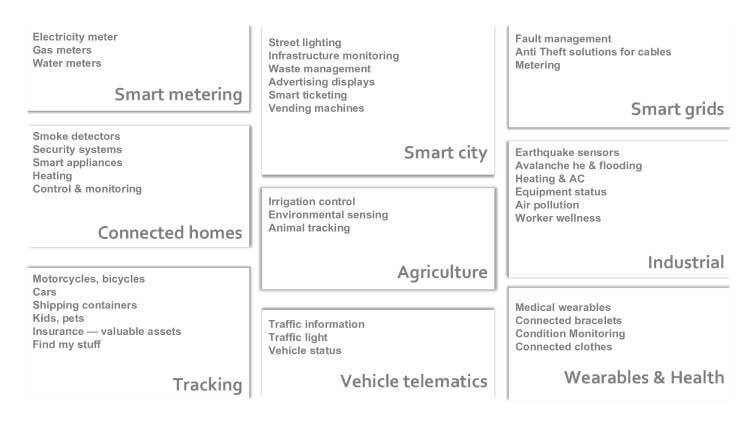
As mentioned before, LoRa allows for low power, long range but low data rates. Typical use cases can be found in the IoT (Internet of Things), IoE (Internet of Everything) or M2M (Machine to Machine) area. We’re typically looking at (small) sensors/devices/things that are battery operated and communicate limited information on a limited interval.
Some examples of use cases:
- Metering:
- Sends 1 to 5 messages a days about the current usage
- For example: gas/water/electricity
- >10 years on battery
- Smart parking:
- Sends a message when a vehicle arrives or leaves a parking spot
- Can be combined with an app to find a free parking spot
- No cabling required, low maintenance
- Smart bin:
- Sends a message when a trash can is full
- Optimise route for garbage collection, save labor and fuel
- Smart lighting:
- Control streetlight status and operation
- Environment monitoring
- For example: sound, temperature, pollution, radiation, humidity,…
- Create valuable insights in combination with geolocation
- Asset management
- Check status and location of various assets
- Control relays, locks, lights,…
- Healthcare
- For example: activity/fall detection, personal alarm, surveillance
- No need for charging, great network coverage
- Tracking
- Track goods, vehicles, animals
Conclusion
For most people, Sigfox is not an option—the network is not available everywhere. LoRa, however, is an option for most people because, with this, you can set up and manage your own network. That aside, both are equivalent when it comes to use cases, with a few caveats to be aware of.
LoRa is likely the better option if you need true bidirectionally because of the symmetric link. So if you need command-and-control functionality—for, say, electric grid monitoring—LoRa is your best option.
With Sigfox, you could use bidirectional command-and-control functionality,; but to work appropriately, network density would need to be higher (due to the asymmetric link). Therefore, it is better for applications that send only small and infrequent bursts of data, like alarms and meters.
Other than these minor differences, Sigfox and LoRa serve similar markets. It’s worth noting that both technologies were originally designed for the European regulatory bands between 865 and 868 MHz, and they’ve both faced challenges in coming over to the regulated markets in the U.S. Progress is being made, and both technologies are working toward optimization for FCC use.
What is Passwordless Authentication?
Dear Readers, The blog of this week is about a passwordless authentication system Through this blog, we aim to make our readers aware of passwordless authentication and how it has the potential to provide convenient access and strengthened security that today’s...
Enterprise Security Threats
Dear Readers, This week’s blog is about Enterprise Security Threats; as enterprise organizations adopt new technologies for their business, they also expand their digital attack surface and introduce additional network vulnerabilities that attackers can exploit. For...
Cyber Attacks in India
Dear Readers, This is our attempt to analyze Online security in India by looking at some of the biggest Cyber Attacks in India. We have to break it down into three articles, this being the first of the three parts. AmbiSecure with its mission to safeguard our highly...
Features to consider on route to digital transformation
Dear Readers, This week’s blog is about features to consider on the route to digital transformation. Recently, corporate digital transformation strategies to the cloud have accelerated instantaneously and effectively, supporting the new hybrid work environment. While...
Security Tips
Dear Readers, This week’s blog is about Tightening your security and how passwords are the keys to most devices and almost everything you do online. Unfortunately, even the best passwords can get hacked, stolen, or unintentionally shared. But fortunately, there is an...
Perils to circumvent when shifting to passwordless technology
Dear Readers, This week’s blog is about how organizations are being forced to move away from passwords. They are specifically asked to justify the costs associated with password support, reevaluating the impact on user experience and, most importantly, justifying...



Recent Comments