Dear Readers,
In the realm of cryptography, the distinction between symmetric and public-key encryption plays a fundamental role in securing digital communications. Symmetric key encryption, characterized by its use of a single shared key for both encryption and decryption, is a cornerstone of secure data transfer. On the other hand, public-key encryption employs a pair of distinct keys, one for encryption and one for decryption, offering enhanced security and key management capabilities. Understanding the differences between these two encryption methods is essential for safeguarding sensitive information in the digital age, as they each have their unique strengths and applications in the realm of data security.
What is a Symmetric Key?
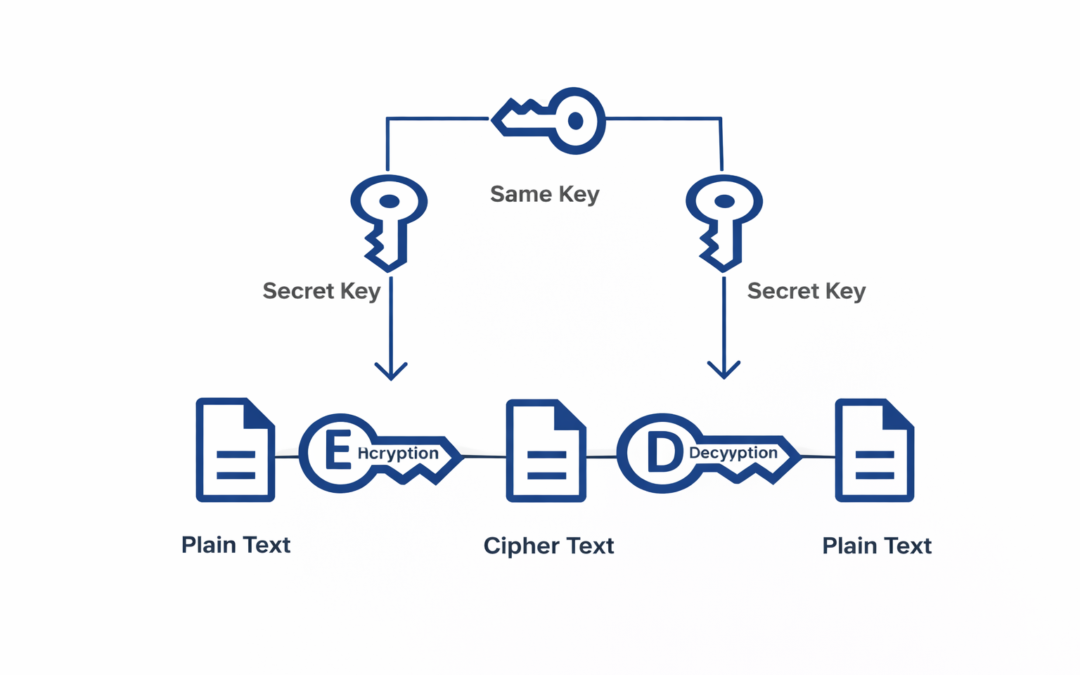
In cryptography, a symmetric key is one that is used both to encrypt and decrypt information. This means that to decrypt information, one must have the same key that was used to encrypt it. The keys, in practice, represent a shared secret between two or more parties that can be used to maintain a private information link. This requirement that both parties have access to the secret key is one of the main drawbacks of symmetric key encryption, in comparison to public-key encryption.
Public Key Encryption
When the two parties communicate to each other to transfer the intelligible or sensible message, referred to as plaintext, is converted into apparently random nonsense for security purpose referred to as ciphertext.
Encryption:
The process of changing the plaintext into the ciphertext is referred to as encryption.
The encryption process consists of an algorithm and a key. The key is a value independent of the plaintext.
The security of conventional encryption depends on the major two factors:
- The Encryption algorithm
- Secrecy of the key
Once the ciphertext is produced, it may be transmitted. The Encryption algorithm will produce a different output depending on the specific key being used at the time. Changing the key changes the output of the algorithm.
Once the ciphertext is produced, it may be transmitted. Upon reception, the ciphertext can be transformed back to the original plaintext by using a decryption algorithm and the same key that was used for encryption.
Decryption:
The process of changing the ciphertext to the plaintext that process is known as decryption.

Recent Comments