
by Ciright | Jan 22, 2026 | Blogs, Uncategorized
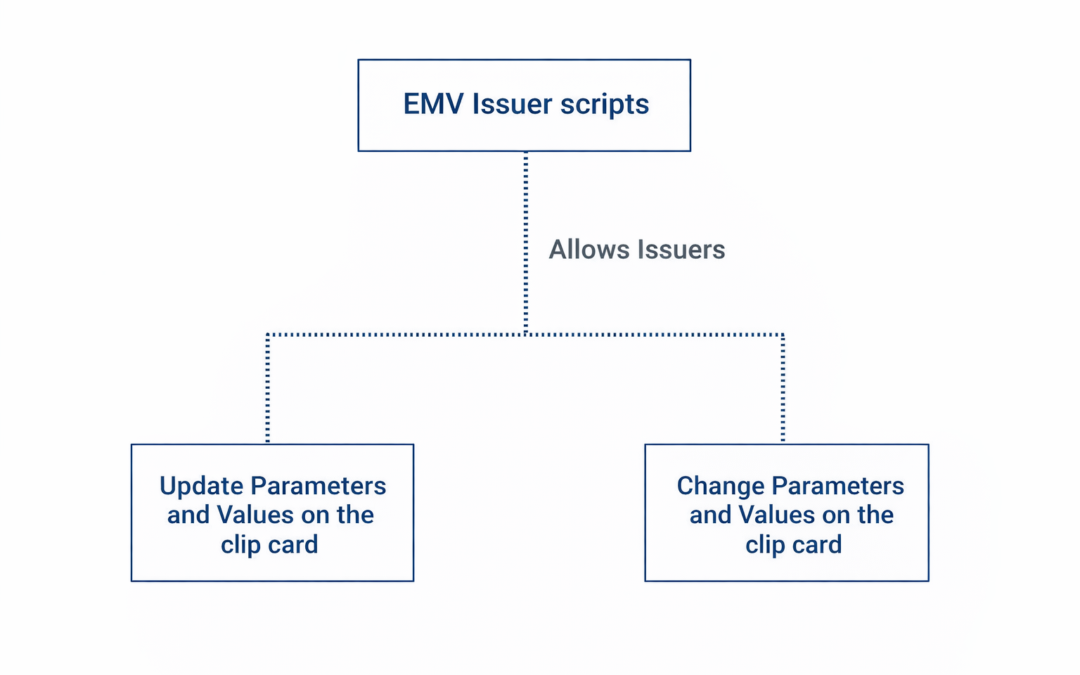
Dear Readers, In this blog we are going to learn about EMV Issuer scripts and how do they work. EMV Issuer scripts allow the Issuer to update and change parameters and values on the card chip whilst it is live in the field. This means that the EMV application can be...

by Ciright | Jan 22, 2026 | Blogs, Uncategorized
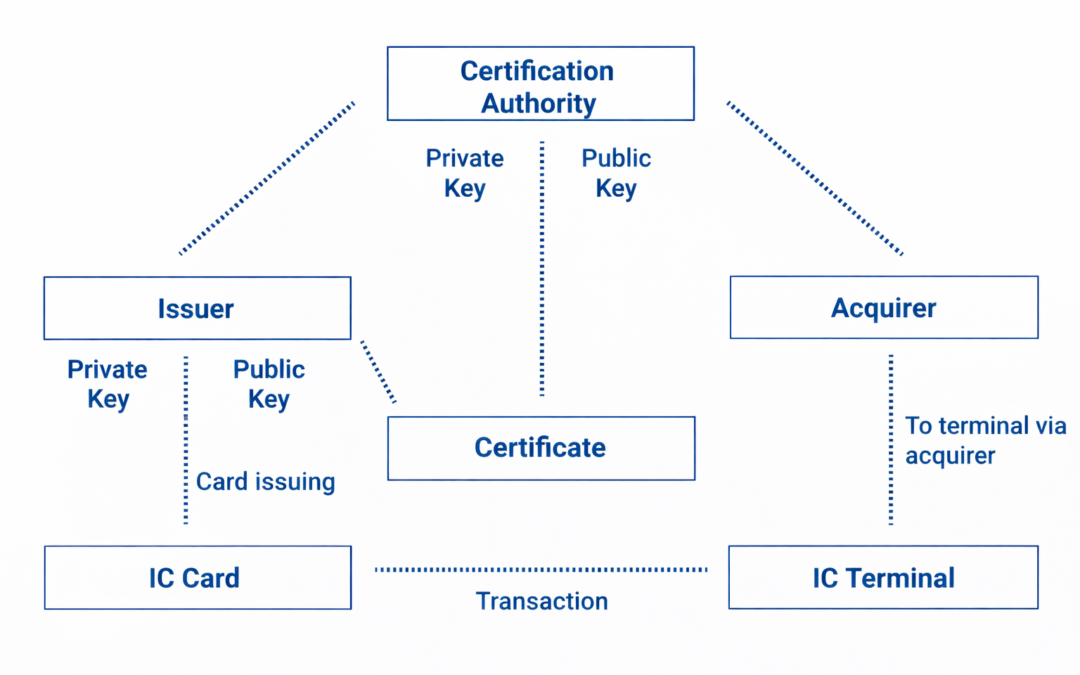
Dear Readers, EMV Certificate Authority The Cryptomathic EMV CA is an essential service component for EMV card authentication. The main purpose of the EMV CA is to allow a central authority to issue and manage the certificates of Card Issuers within a given region....

by Ciright | Jan 22, 2026 | Blogs, Uncategorized
Dear Readers, This blog post delves into the differences between HiCo (High Coercivity) and LoCo (Low Coercivity) magnetic stripe cards. While both can store the same amount of data, HiCo cards, characterized by their black color and stronger magnetic encoding (2750...

by Ciright | Jan 22, 2026 | Blogs, Uncategorized
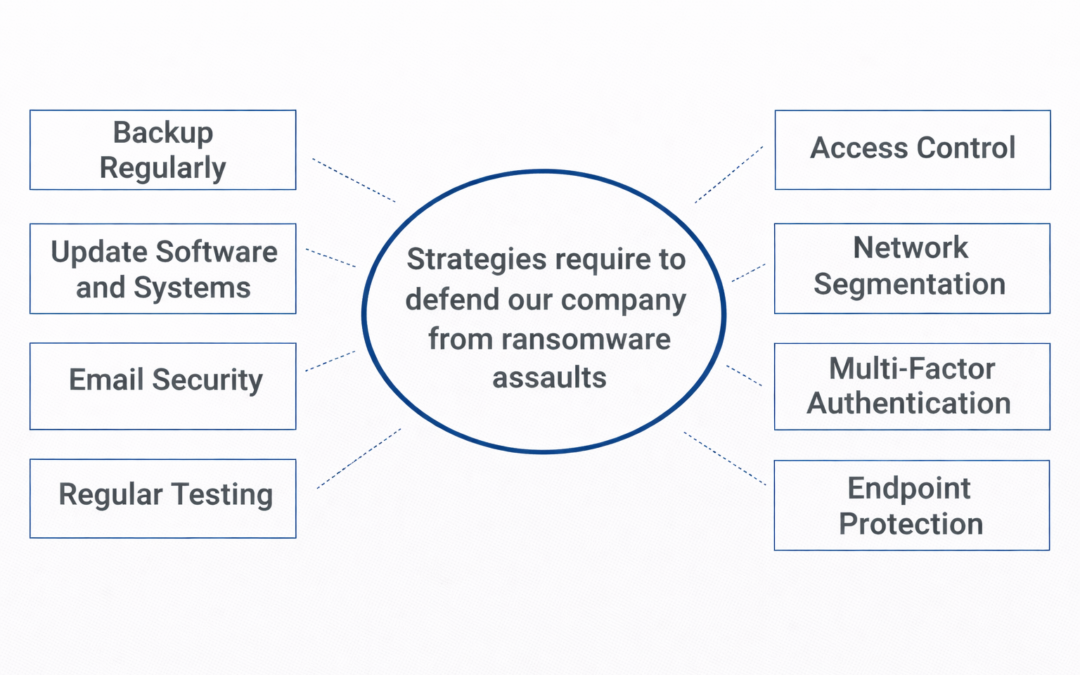
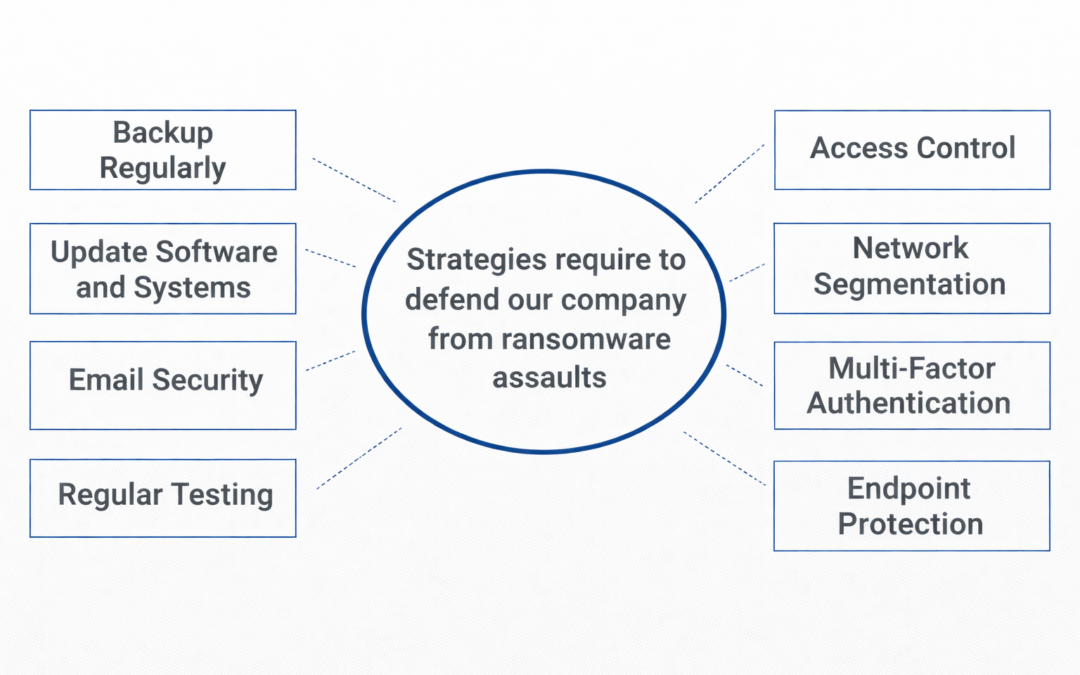
Dear Readers, Businesses must take proactive measures to safeguard themselves against financial losses as the frequency of ransomware attacks rises. We’ll discuss some of the best strategies for protecting your business from ransomware attacks in this post. Make...

by Ciright | Jan 22, 2026 | Blogs, Uncategorized
Dear Readers, Due to the volume of private patient data handled often, the healthcare sector is a favourite target for hackers. It is more crucial than ever to make sure that the sector is ready to defend itself against cyber attacks as healthcare providers’...

by Ciright | Jan 22, 2026 | Blogs, Uncategorized
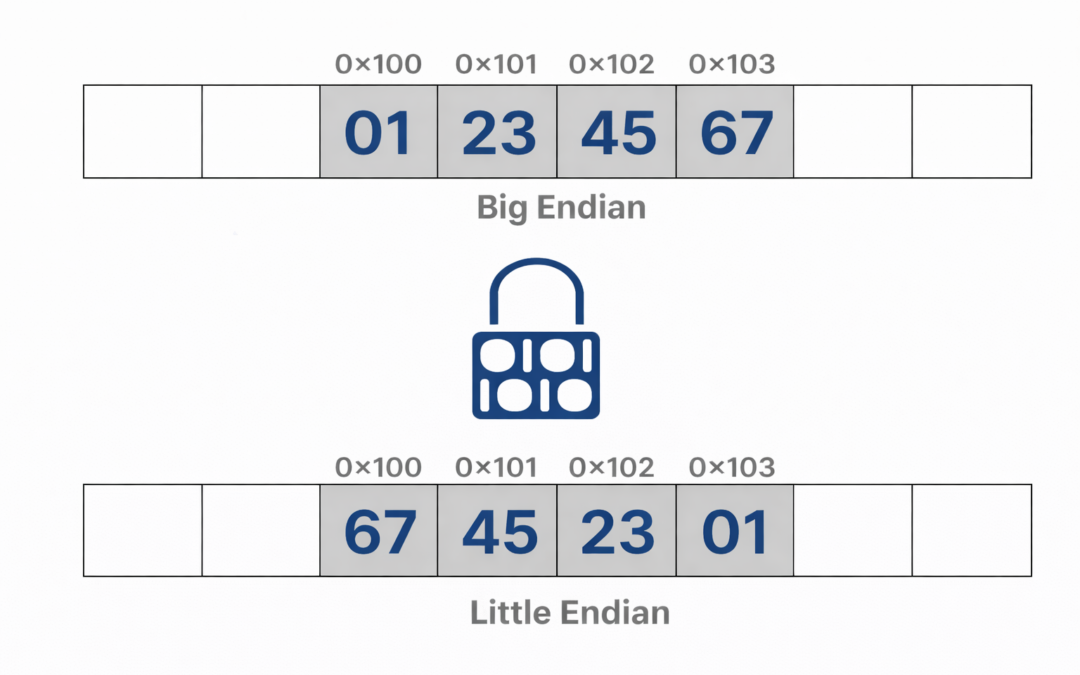
Dear Readers, In this blog we are going to learn about, Byte order, or endianness, is a fundamental issue in computing where machines interpret and store multi-byte data, such as integers, differently. This text explores the challenges posed by byte order...



Recent Comments