
by Ciright | Jan 23, 2026 | Blogs
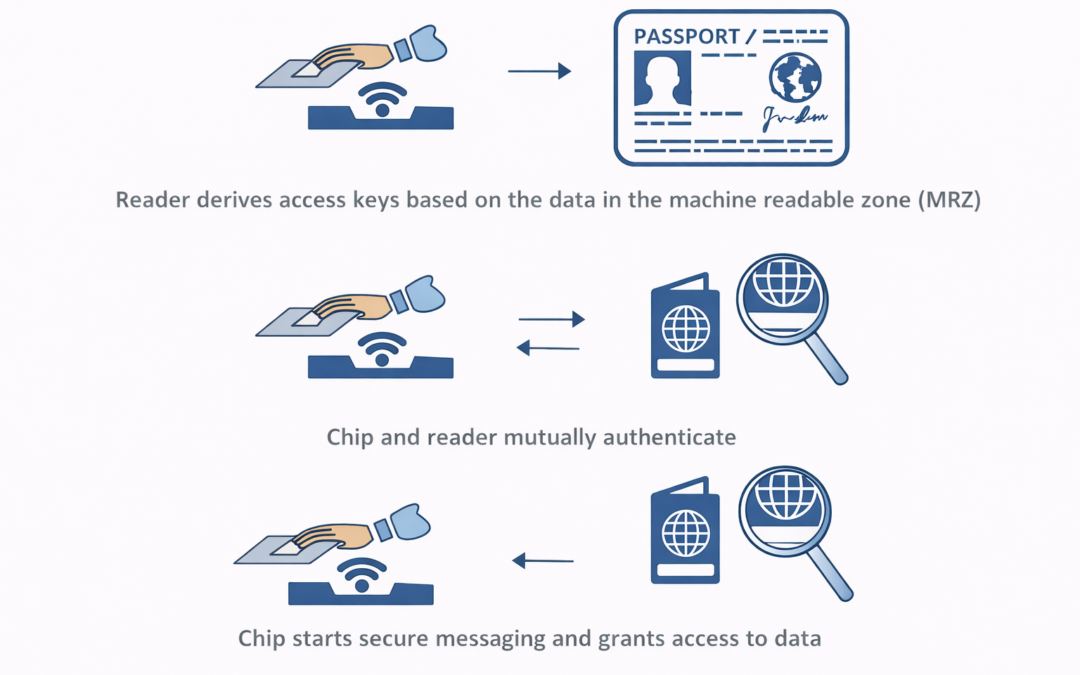
Dear Readers, This week’s blog is how a biometric passport is expected to enable technological advancement? What is the Most Important Application of e-passport or biometric identification card? Ambimat Electronics, with its experience of over four decades as an ODM...

by Ciright | Jan 23, 2026 | Blogs
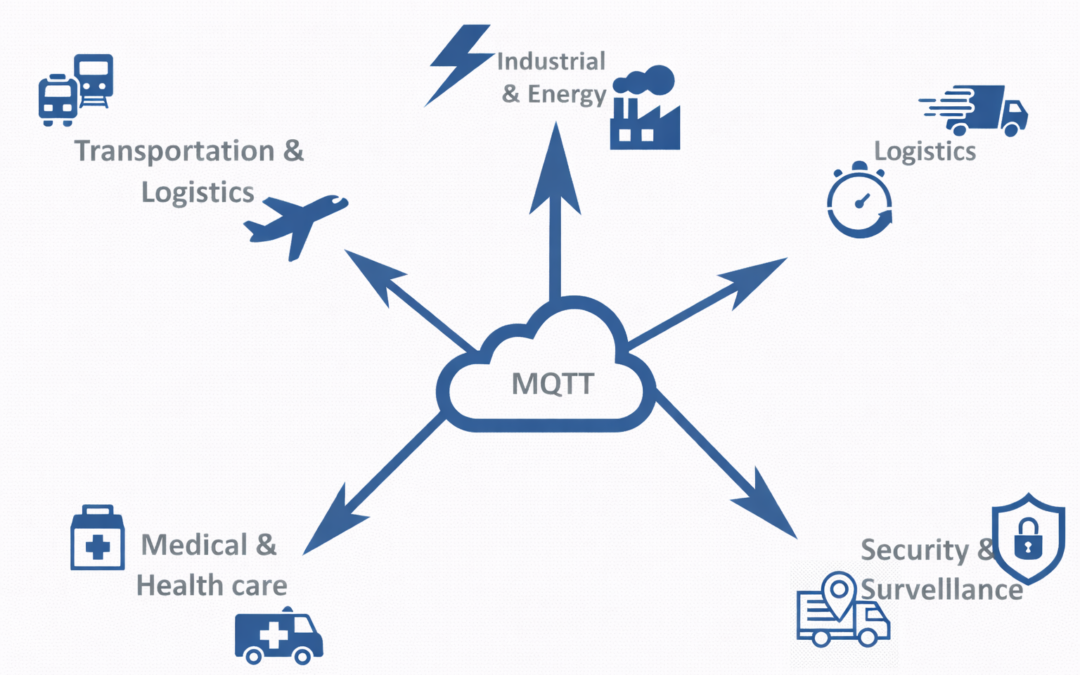
Dear Readers, This week’s blog is an introduction to MQTT-SN (MQTT for Sensor Networks) and how it is designed specifically for efficient operation in large low-power IoT sensor networks. Ambimat Electronics, with its experience of over four decades as an ODM of IoT...

by Ciright | Jan 23, 2026 | Blogs
Dear Readers, In this week’s blog, we try to understand why we’re amid a Global Semiconductor Shortage. How these Shortages of semiconductors have been hurting manufacturers of automobiles, Laptops, and Consumer electronics; they are struggling to meet demand because...

by Ciright | Jan 23, 2026 | Blogs
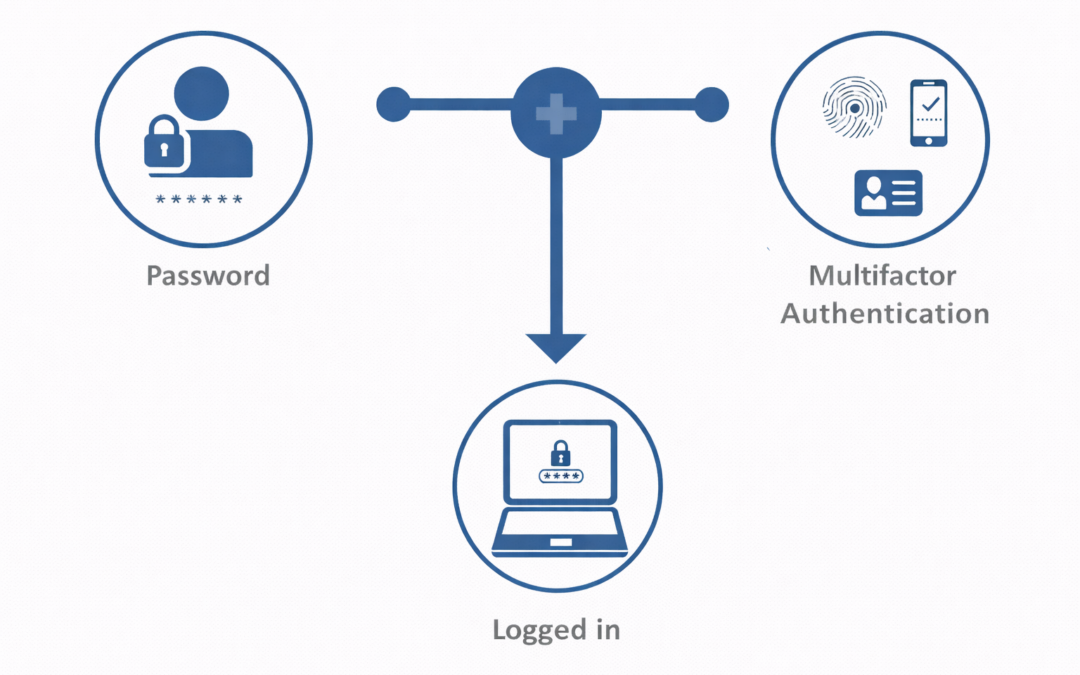
Dear Readers, This week’s blog is What is MFA(Multi-Factor Authentication)? MFA is quite simple, and organizations are focusing more than ever on creating a smooth user experience. Governments are implementing a Multi-Factor Authentication system. Ambimat Electronics,...

by Ciright | Jan 23, 2026 | Blogs
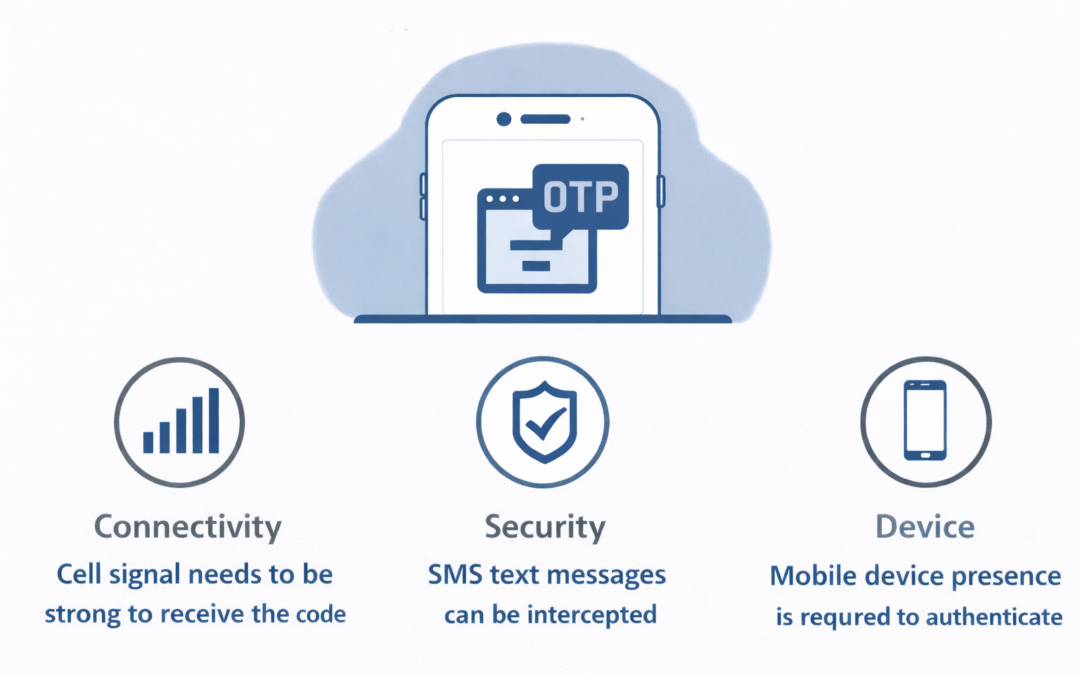
Dear Readers, The blog of this week is about the Limitations of SMS-based OTP Authentication. Through this blog, we aim to make our readers aware of the common two-factor authentication (2FA) techniques used In India have several shortfalls. We take a look at security...

by Ciright | Jan 23, 2026 | Blogs
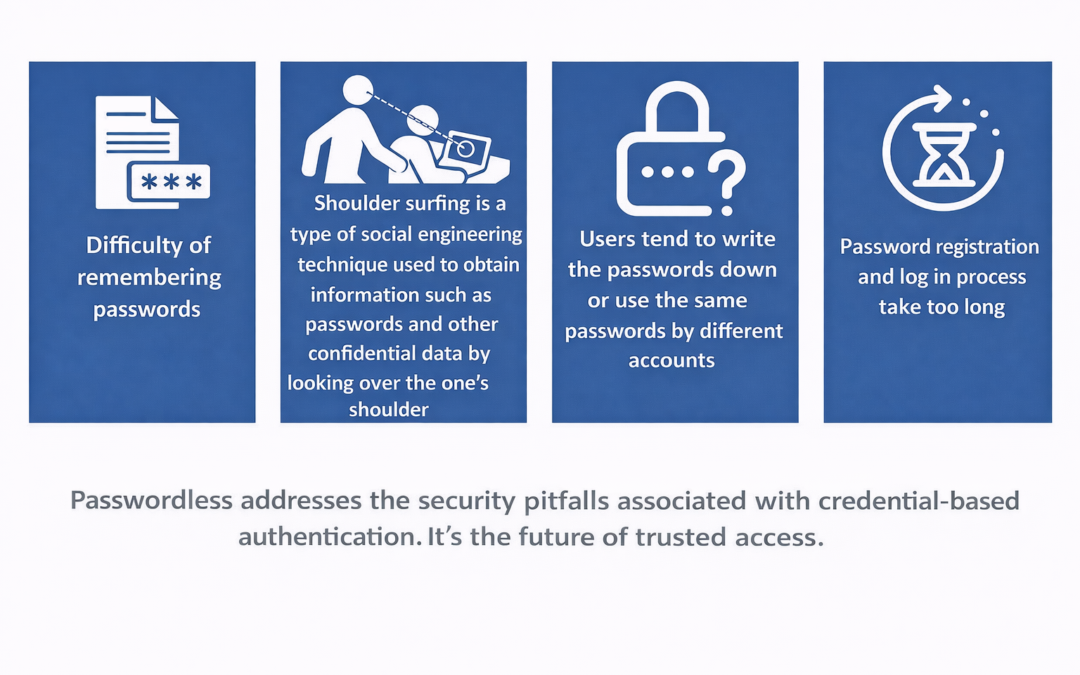
Dear Readers, The blog of this week is about Improving Security Through Passwordless Authentication. Through this blog, we aim to make our readers aware of the common two-factor authentication (2FA) techniques and Improving Security Through Passwordless...


Recent Comments