
by Ciright | Jan 22, 2026 | Blogs
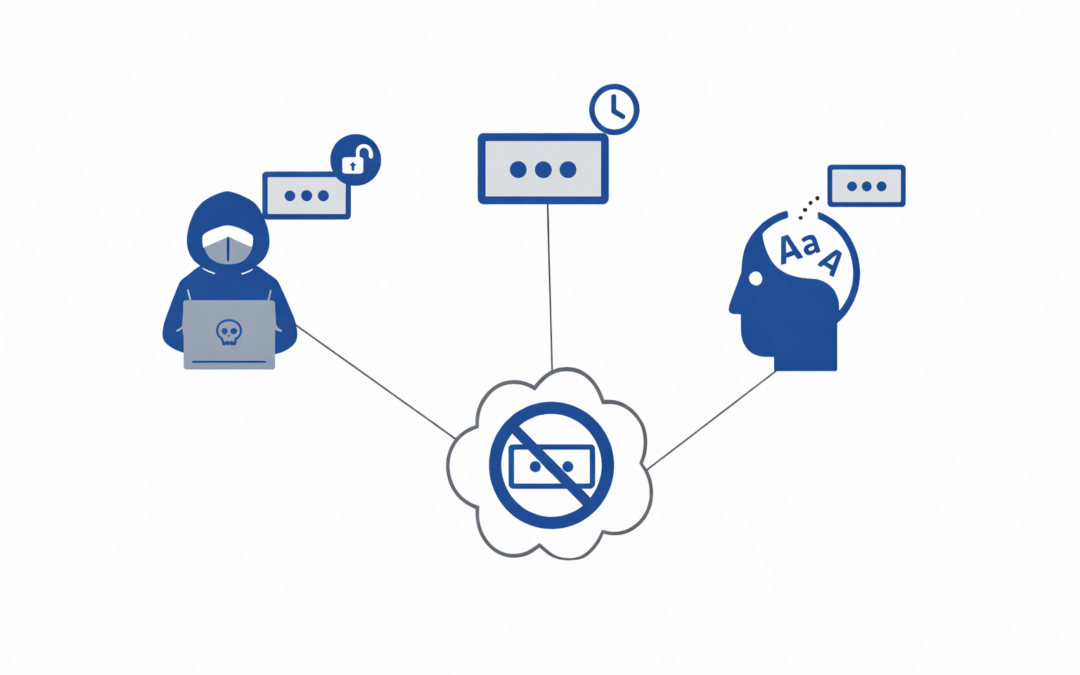
not without problems that make them less than ideal for securing our digital identities. As a result, many experts believe that a future without passwords is essential. This blog post will go through some of the reasons why a password-free future is necessary. Hackers...

by Ciright | Jan 22, 2026 | Blogs
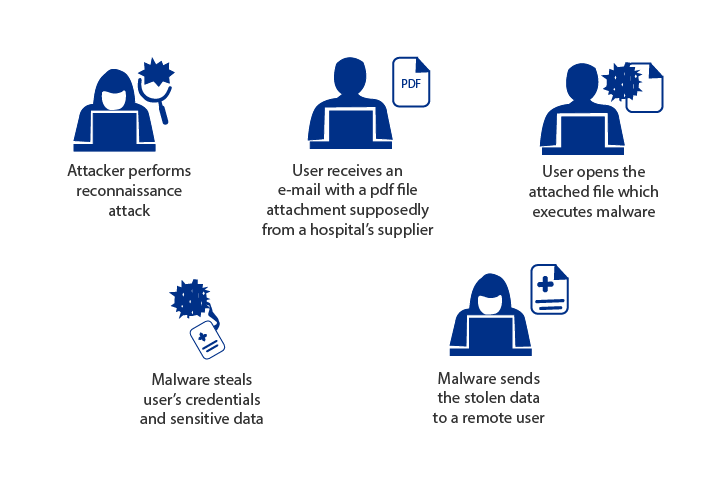
Dear Readers, This week’s blog is about taking a closer look at the rise of social engineering attacks and explaining why it is so important to be vigilant, seek out IT support services, and provide the proper training for your employees. Cyber security threats of all...

by Ciright | Jan 22, 2026 | Blogs
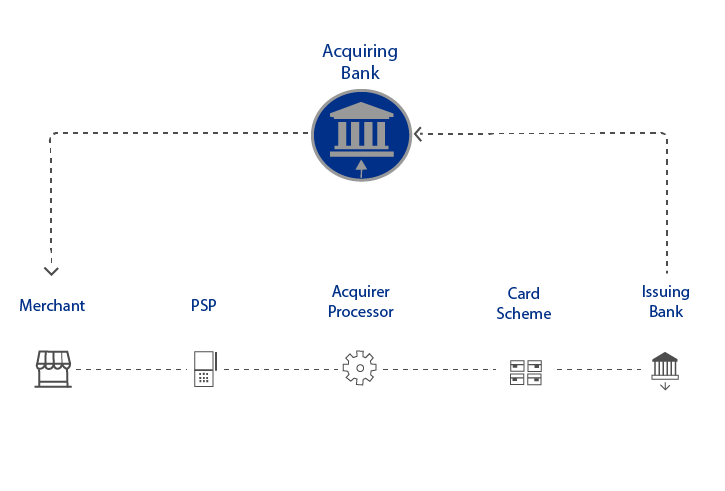
Dear Reader, An acquiring bank (also known simply as an acquirer) is a bank or financial institution that processes credit or debit card payments on behalf of a merchant. The acquirer allows merchants to accept credit card payments from the card-issuing banks within a...

by Ciright | Jan 22, 2026 | Blogs
Dear Readers, To prevent fraud and identity theft in today’s digital era, governments and organizations all over the world are investing in secure identification systems. Passports, driver’s licenses, and national ID cards are important tools for establishing and...

by Ciright | Jan 22, 2026 | Blogs
Dear Readers, Phishing is a type of cyberattack where a perpetrator attempts to get sensitive information from a victim by pretending to be a reputable company. This type of assault may be launched by email, text message, or social media. In this post, we’ll take a...

by Ciright | Jan 22, 2026 | Blogs
Dear Readers, In this blog we are going to learn about, The Wiegand interface, stemming from the 1980s popularity of Wiegand effect card readers, has become a de facto wiring standard for connecting card swipe mechanisms to access control systems. This interface...



Recent Comments