
by Ciright | Jan 22, 2026 | Blogs
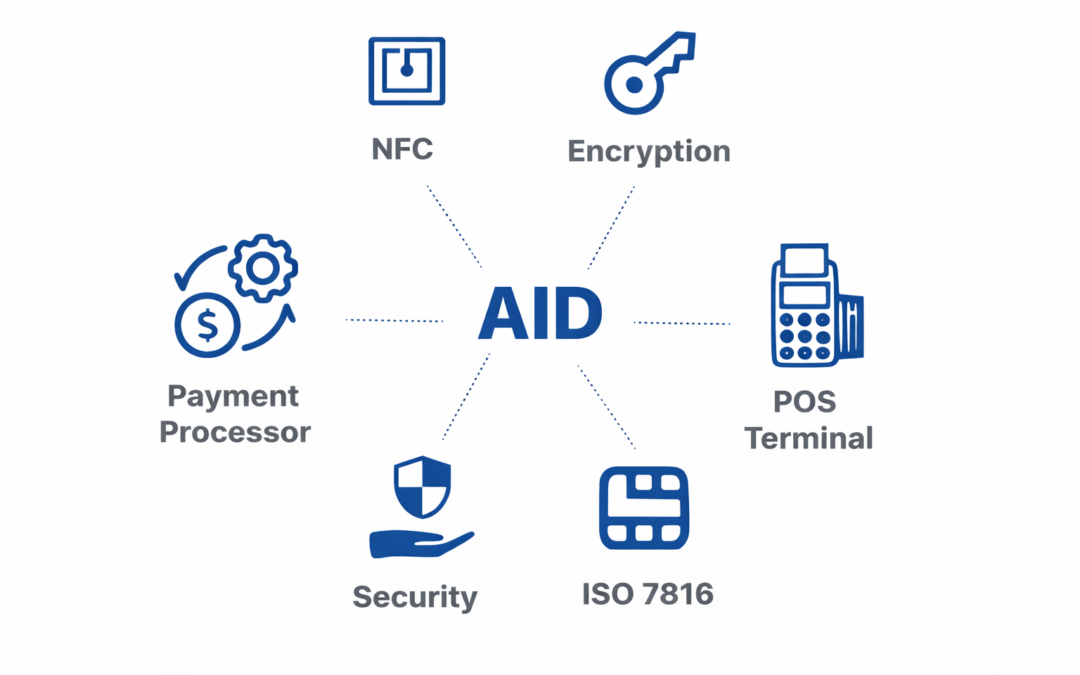
Dear Readers, below is the Complete list of Application Identifiers (AID) List of AID’s with their description. AID(Application Identifier)VendorCountryNameDescriptionType315041592E5359532E4444463031Visa InternationalUnited StatesVisa Payment System Environment – PSE...

by Ciright | Jan 22, 2026 | Blogs
Dear Readers, As technology evolves and becomes more intertwined into our daily lives, the notion of a digital identity wallet is gaining traction. As a result, citizens’ expectations of what such a wallet should be able to perform have shifted. Citizens, first and...

by Ciright | Jan 22, 2026 | Blogs
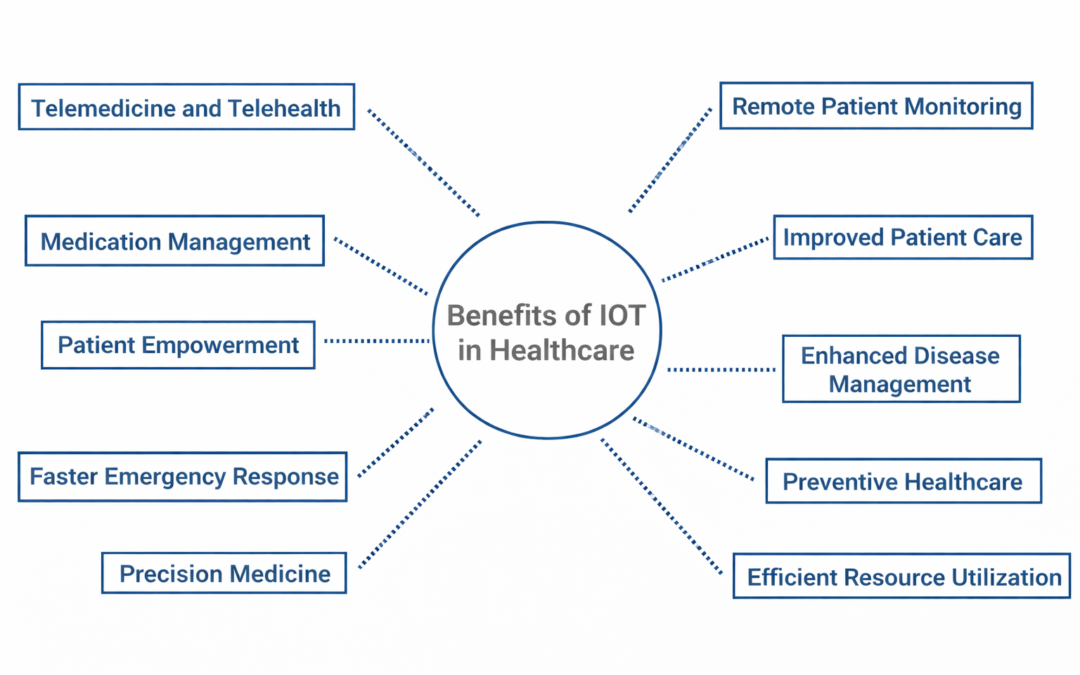
Dear Readers, By enabling medical equipment, wearables, and other connected devices to communicate data to healthcare practitioners in real-time, IoT, also known as the Internet of Things, has the potential to completely transform the healthcare sector. This may...

by Ciright | Jan 22, 2026 | Blogs
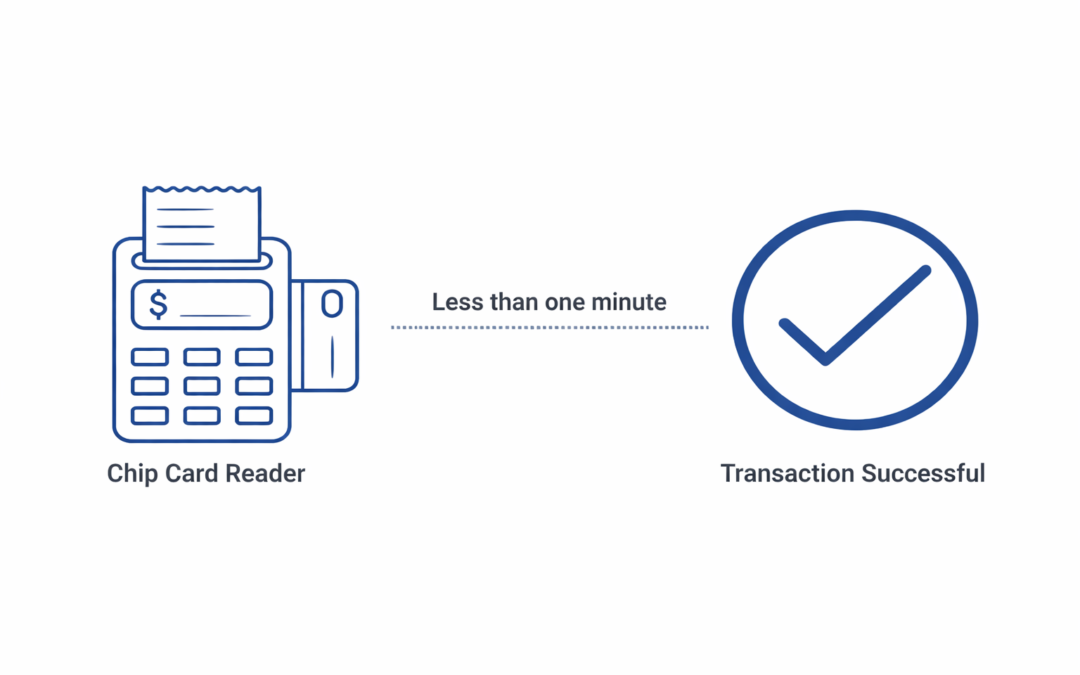
Dear Readers, In this blog we are going to learn about “Chip card transactions faster than a New York minute” signifies the rapidity and efficiency of modern chip card payment methods. With the widespread adoption of EMV (Europay Mastercard Visa) chip technology,...

by Ciright | Jan 22, 2026 | Blogs
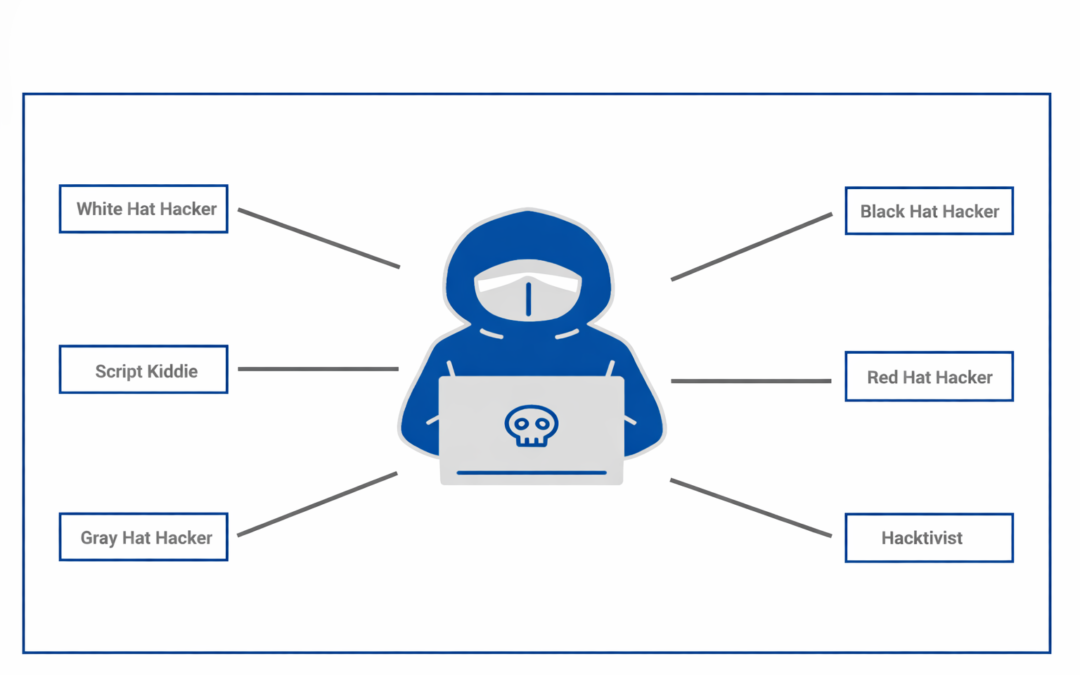
Dear Readers, As the world becomes increasingly reliant on technology, cybersecurity threats are becoming more prevalent. Hackers have evolved from the stereotypical image of a person sitting in a dark basement, typing away on a computer, to a diverse range of...

by Ciright | Jan 22, 2026 | Blogs
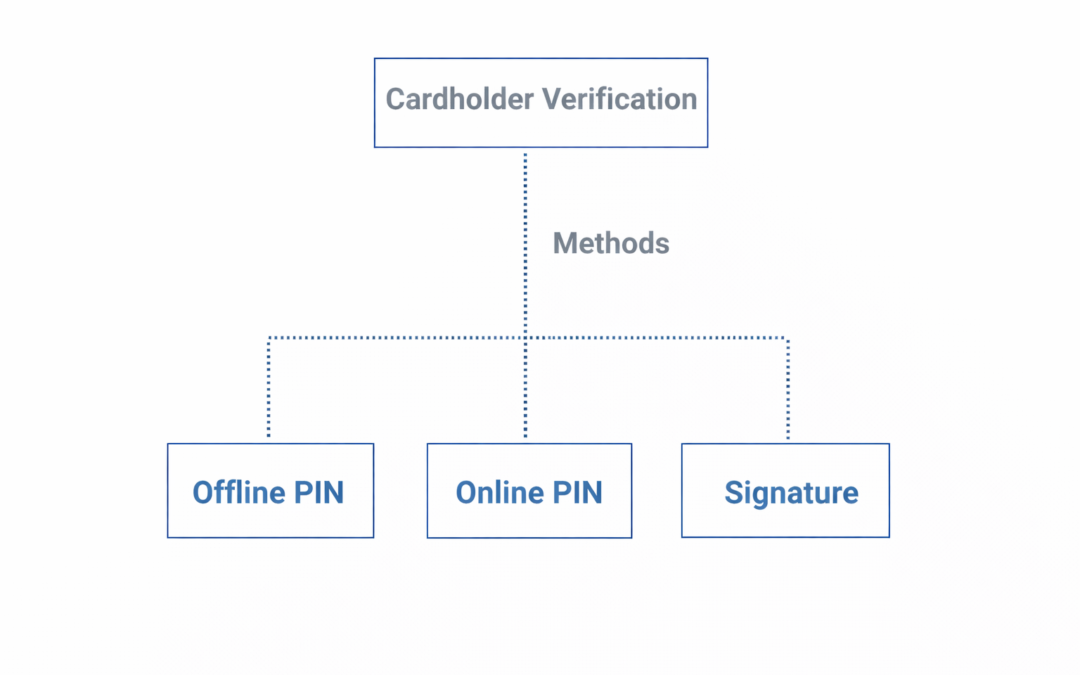
Dear Readers, This article has been written to provide a brief introduction to cardholder verification with EMV and the challenges posed by different verification methods. One objective of EMV was to drive down fraud; to do this we need to prove three things: The bank...



Recent Comments