
by Ciright | Jan 22, 2026 | Blogs
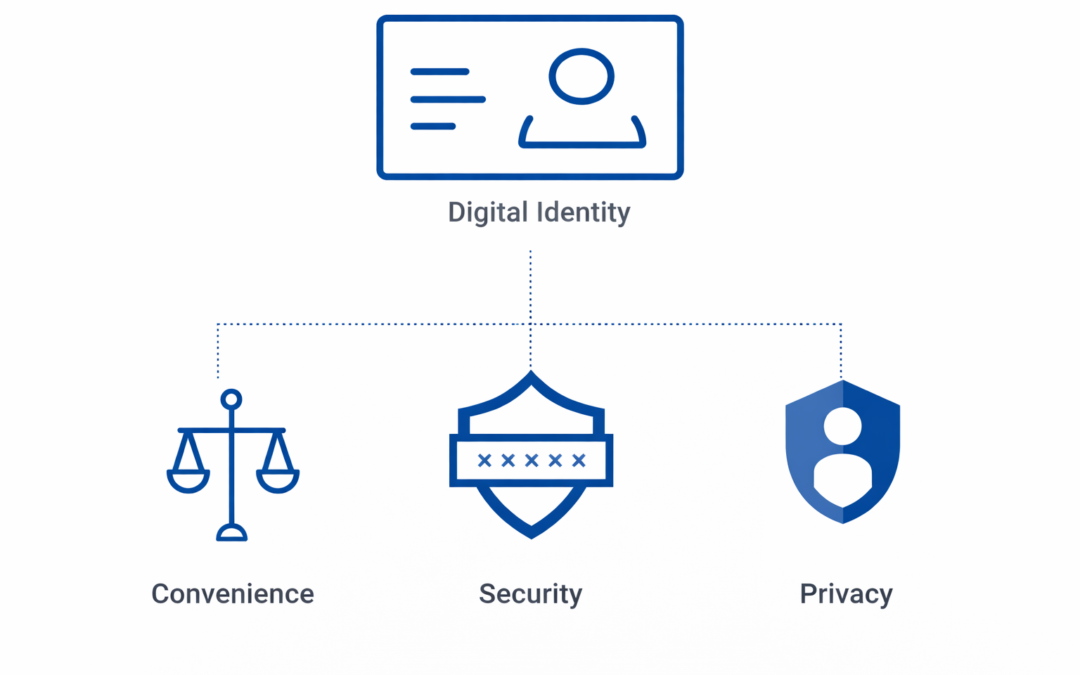
Dear Readers, The three pillars of digital identification are convenience, security, and privacy. Our internet identities are equally as vital as our physical ones in today’s environment. We rely on them for everything from bank account access to social media login....

by Ciright | Jan 22, 2026 | Blogs
Dear Readers, This week’s blog is about User experience with passwordless authentication. Passwords require ongoing management from both users and IT staff. For the average user, keeping track of ever-multiplying passwords of varying complexity is, at minimum, a...

by Ciright | Jan 22, 2026 | Blogs
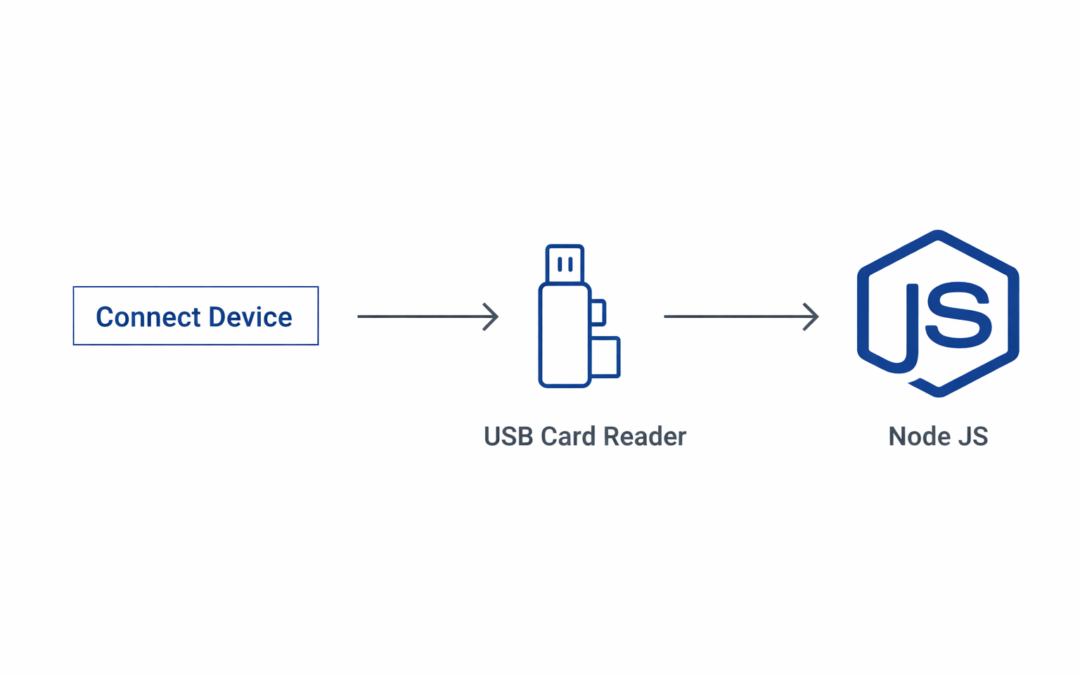
Dear Readers, A really handy thing to be able to do is to control USB devices using JavaScript. This is a powerful capability, made easily possible by NodeJS (better known, simply, as Node). To get Node, go here. Node is an increasingly vital piece...

by Ciright | Jan 22, 2026 | Blogs
Dear Readers, What Does CVV Stand For? CVV stands for card verification value. It’s a three- or four-digit number found on most debit and credit cards. There are several other acronyms for this security feature within the industry. The Purpose of CVVs...

by Ciright | Jan 22, 2026 | Blogs
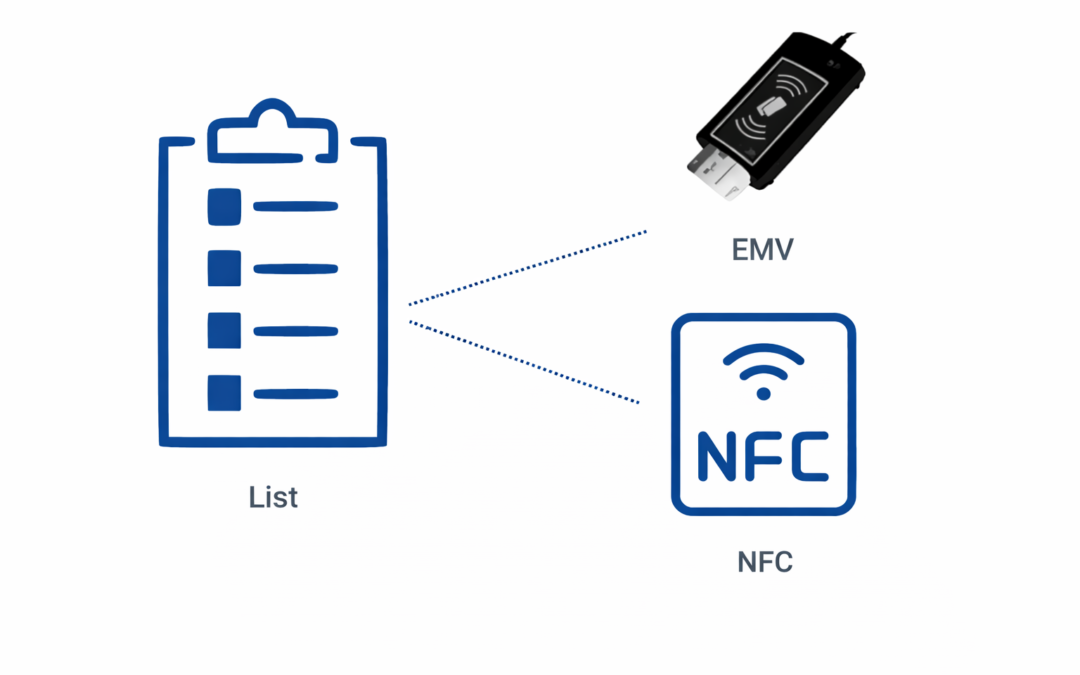
Dear Readers, List of EMV & NFC tags with their description. Note that the same list with extended searching options is implemented in our freeware EFT product. TagNameDescriptionSourceFormatTemplateLength (min)Length (max)P/CExample06Object Identifier...

by Ciright | Jan 22, 2026 | Blogs
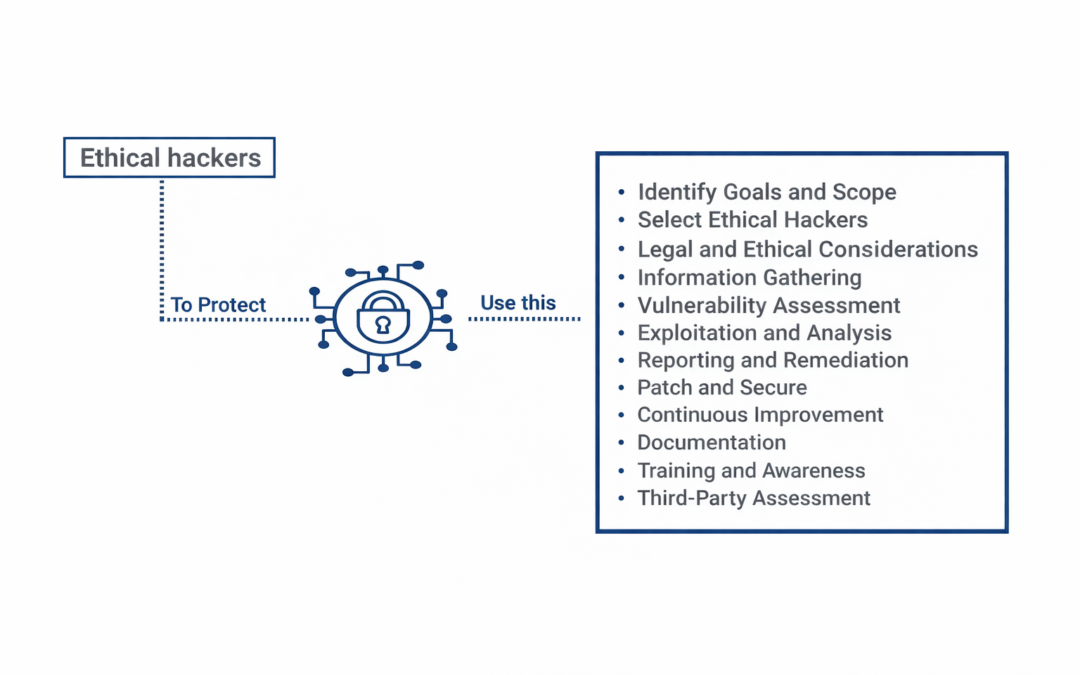
Dear Readers, Cybersecurity assaults are becoming more numerous and complicated by the day, making it increasingly difficult for enterprises to protect themselves. Businesses may secure their data by hiring ethical hackers to uncover flaws in their systems before...



Recent Comments