
by Ciright | Jan 22, 2026 | Blogs
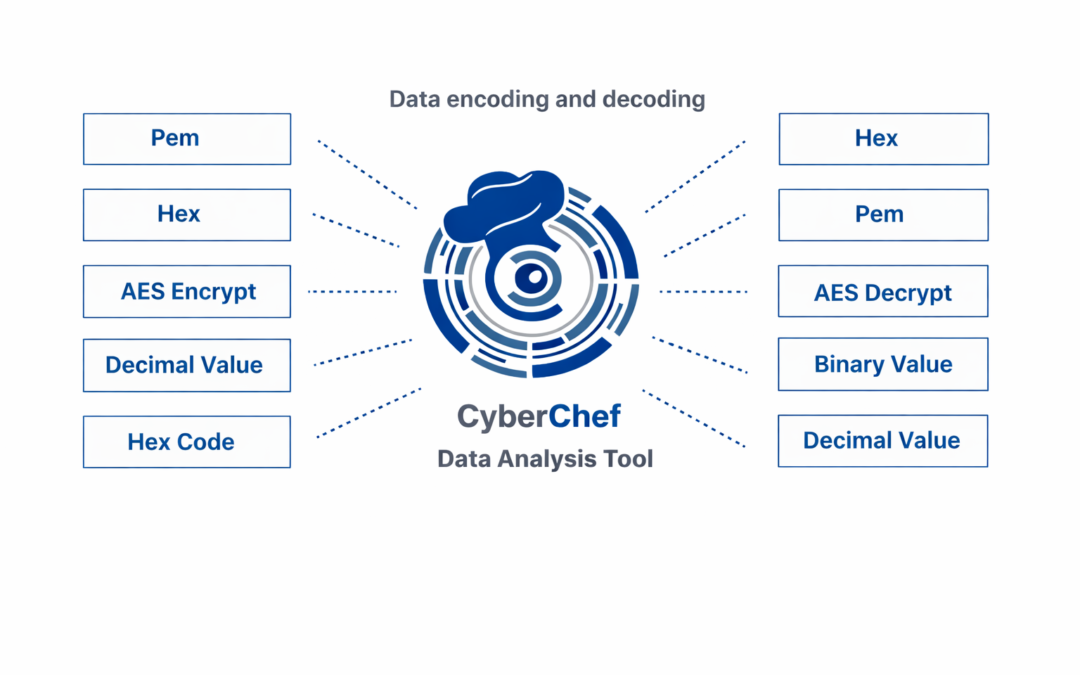
Dear Readers, In this blog we are going to learn, about a Platform known as “CyberChef” which is a free and open-source, web based security analysis tool developed by GCHQ (UK’s Government Communications Headquarters) which is a government intelligence...

by Ciright | Jan 22, 2026 | Blogs
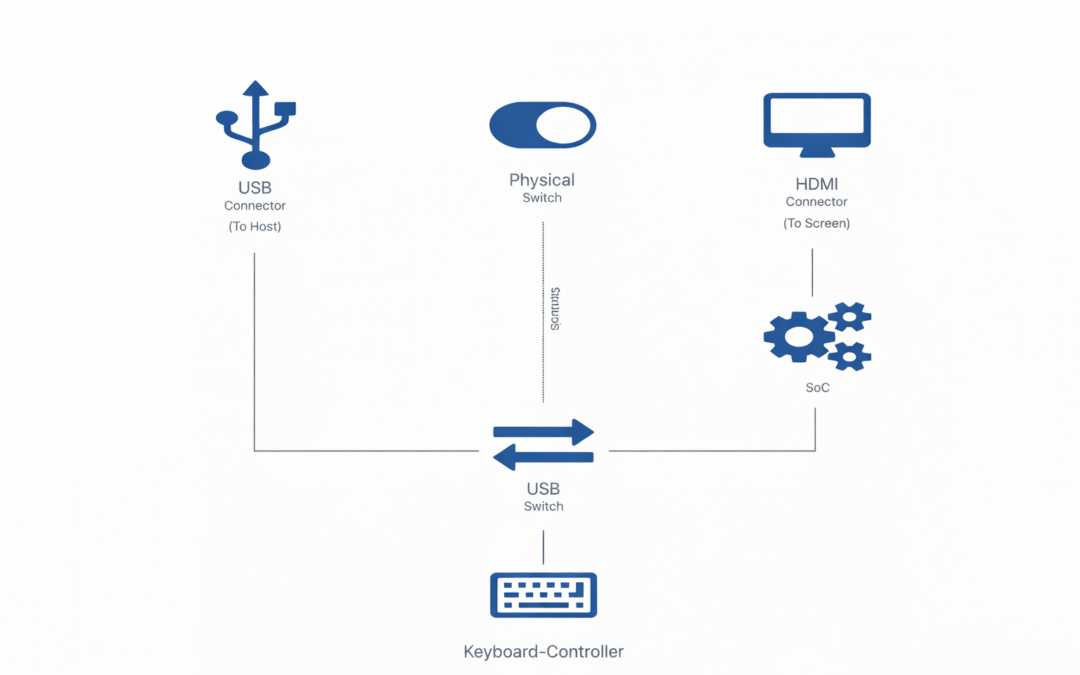
Dear Readers, In this blog we are going to learn about, USB Power Delivery (USB PD) has transformed USB technology from a simple data interface into a versatile power source for a wide range of devices. This evolution, marked by the introduction of USB PD Revision...

by Ciright | Jan 22, 2026 | Blogs
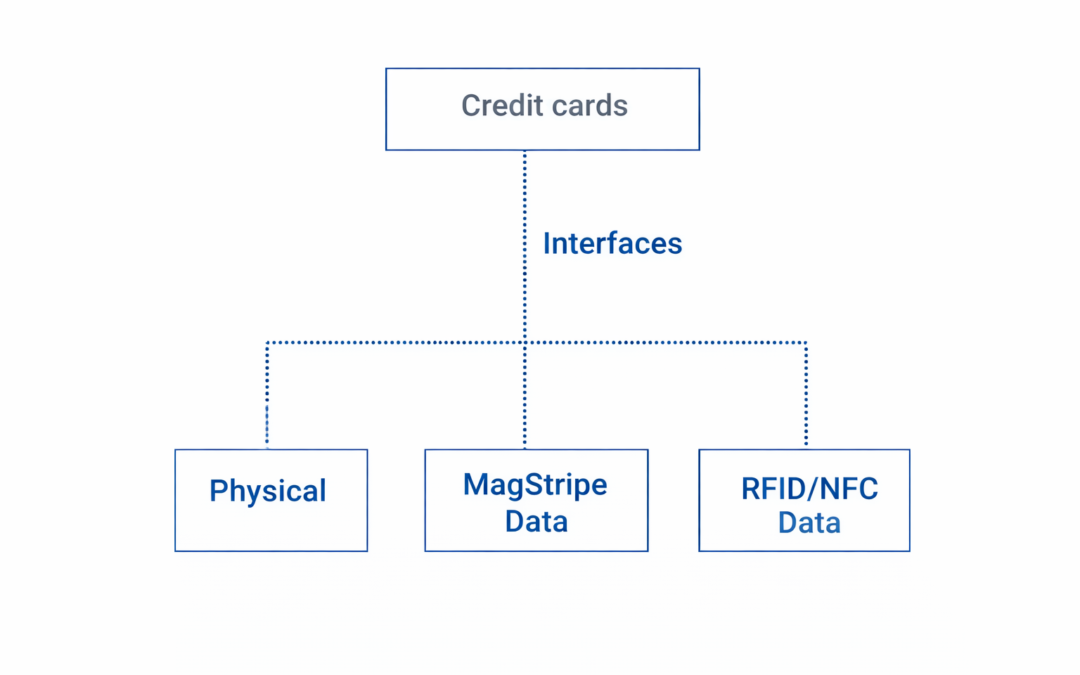
Dear Readers, Modern credit cards in the United States have three interfaces: Physical MagStripe Data RFID/NFC Data This obviously varies from bank to bank and card manufacturer to card manufacturer. The purpose of this post is to evaluate all three interfaces of the...

by Ciright | Jan 22, 2026 | Blogs
Dear Readers, This week’s blog is about Why use Multi-factor Authentication (MFA). By being agile in adopting and deploying efficient security measures like MFA, you can help your business stay agile and competitive in a tight market. The use of multi-factor...

by Ciright | Jan 22, 2026 | Blogs
Dear Readers, The digital revolution has had a significant influence on the music industry, with the emergence of streaming services and digital downloads transforming the way music is consumed and delivered. The COVID-19 epidemic has added a new layer of difficulty,...

by Ciright | Jan 22, 2026 | Blogs
Dear Readers, This week’s blog is about User Adoption of Multi-Factor Authentication. The use of multi-factor authentication is vital, as it ensures that information is only accessed by the intended person, making it harder for cybercriminals to steal. If user data is...



Recent Comments