
by Ciright | Jan 22, 2026 | Blogs, Uncategorized
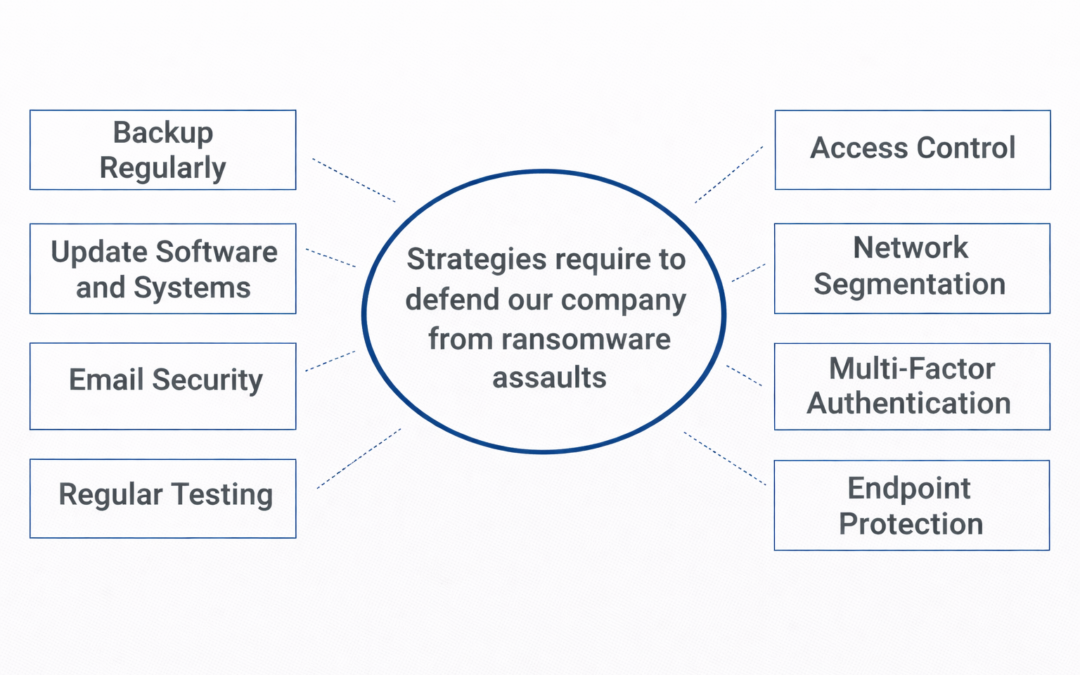
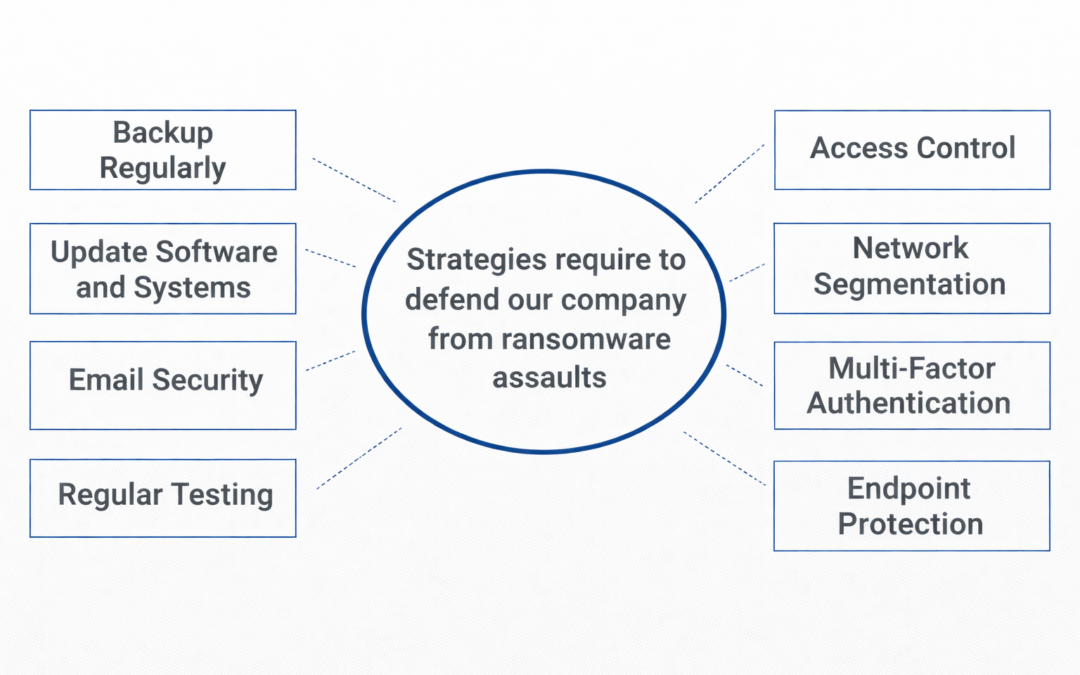
Dear Readers, Businesses must take proactive measures to safeguard themselves against financial losses as the frequency of ransomware attacks rises. We’ll discuss some of the best strategies for protecting your business from ransomware attacks in this post. Make...

by Ciright | Jan 22, 2026 | Blogs
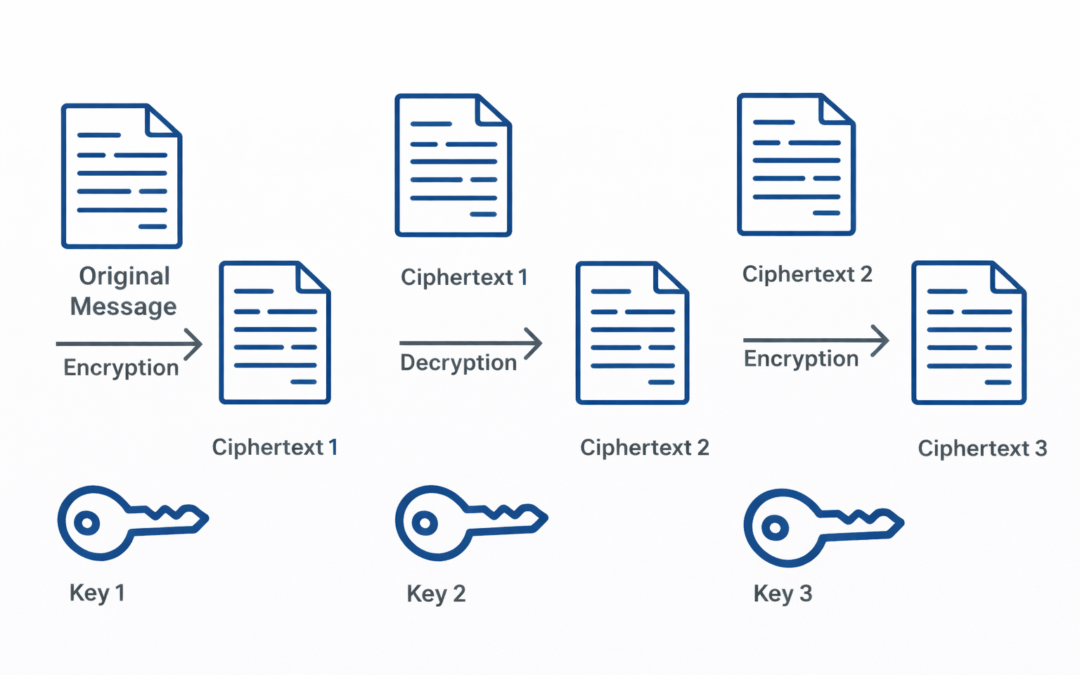
Dear Readers, In this blog we are going to learn about, Triple Data Encryption Standard (3DES), a cryptographic algorithm descended from the original Data Encryption Standard (DES), made its debut in 1998 and has long served as a stalwart protector of data in the...

by Ciright | Jan 22, 2026 | Blogs, Uncategorized
Dear Readers, Due to the volume of private patient data handled often, the healthcare sector is a favourite target for hackers. It is more crucial than ever to make sure that the sector is ready to defend itself against cyber attacks as healthcare providers’...

by Ciright | Jan 22, 2026 | Blogs, Uncategorized
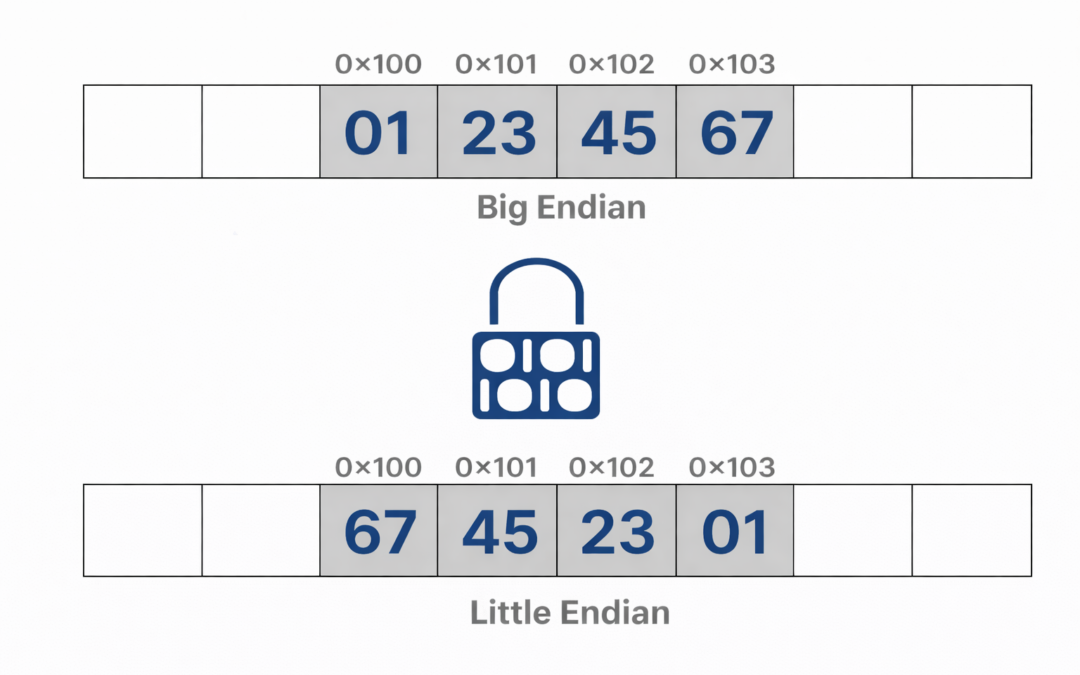
Dear Readers, In this blog we are going to learn about, Byte order, or endianness, is a fundamental issue in computing where machines interpret and store multi-byte data, such as integers, differently. This text explores the challenges posed by byte order...

by Ciright | Jan 22, 2026 | Blogs, Uncategorized
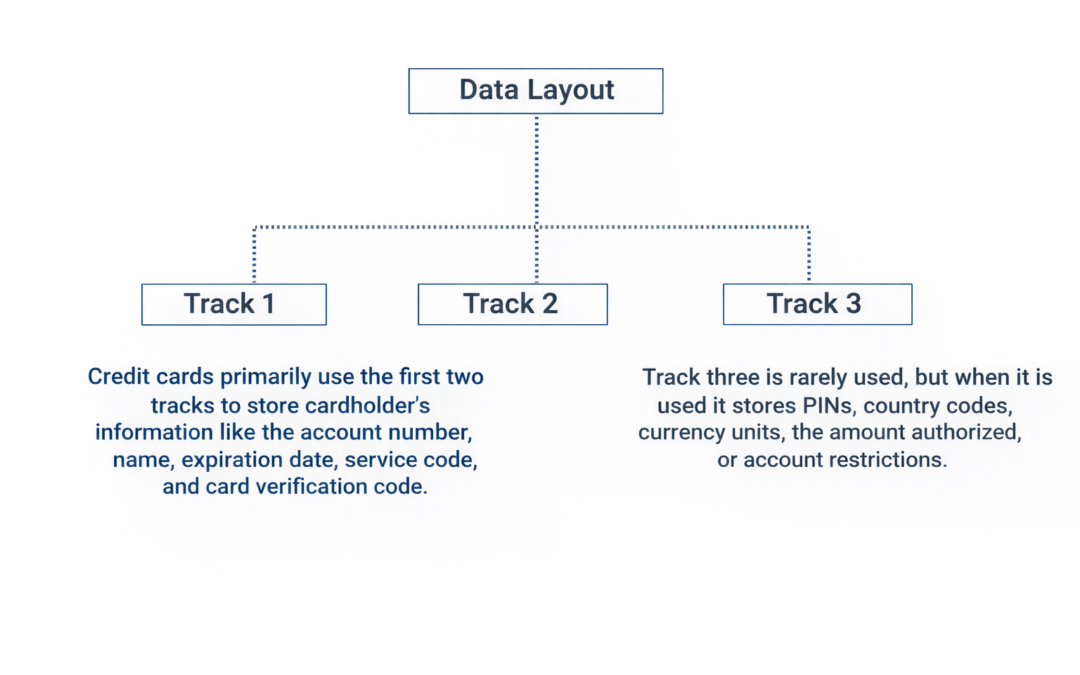
Dear Readers, Data is laid out on a standard magnetic card in three tracks. A magnetic stripe card may have any of these tracks or a combination of these tracks. Track 1 was the first track standardized. The International Air Transportation Association (IATA)...
![USB HID [Human Interface Device]](data:image/gif;base64,R0lGODlhAQABAAAAACH5BAEKAAEALAAAAAABAAEAAAICTAEAOw==)
by Ciright | Jan 22, 2026 | Blogs
Dear Readers, This blog post discusses the USB Human Interface Device (HID) class, an essential part of the USB specification. It standardizes human interface devices used in computing, including keyboards, mice, game controllers, and more. The HID class, governed by...

![USB HID [Human Interface Device]](https://ciright.com/wp-content/uploads/2026/01/USB-HID-Human-Interface-Device-1-1080x675.png)

Recent Comments