
by Ciright | Jan 23, 2026 | Blogs
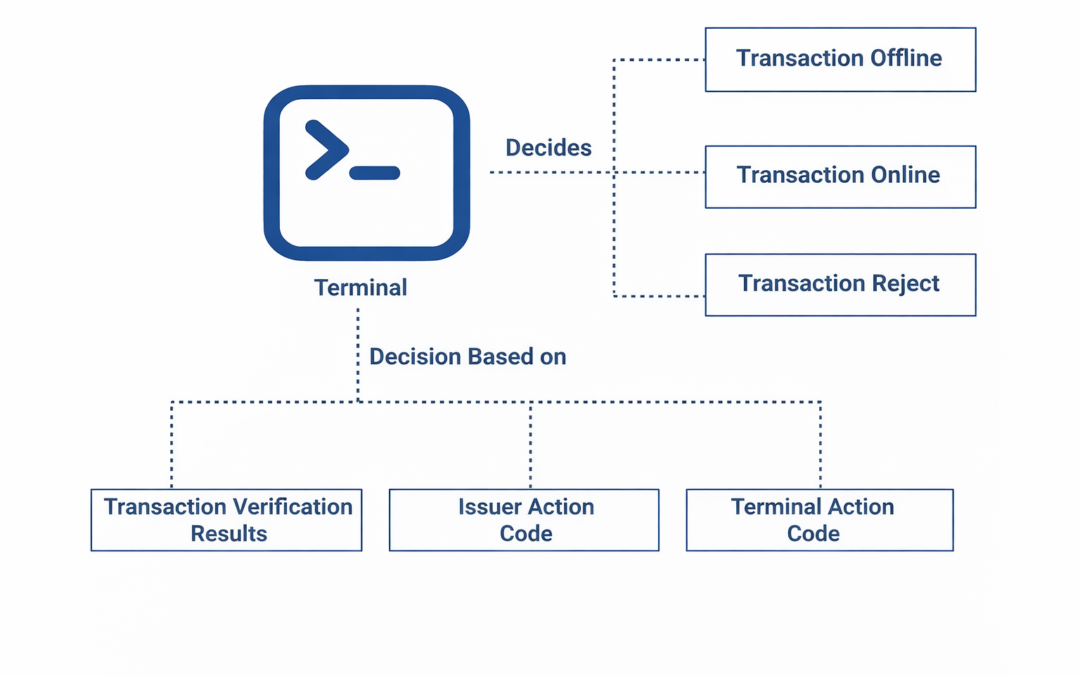
Dear Readers, In the realm of EMV payment processing, understanding the intricate decision-making process that occurs within payment terminals is vital. The terminal’s role in determining whether to proceed with a transaction, seek online authorization, or reject it...

by Ciright | Jan 23, 2026 | Blogs
Dear Readers, This week’s blog is about the passwordless authentication journey. Passwords require ongoing management from both users and IT staff. For the average user, keeping track of ever-multiplying passwords of varying complexity is, at minimum, a hassle and...

by Ciright | Jan 23, 2026 | Blogs
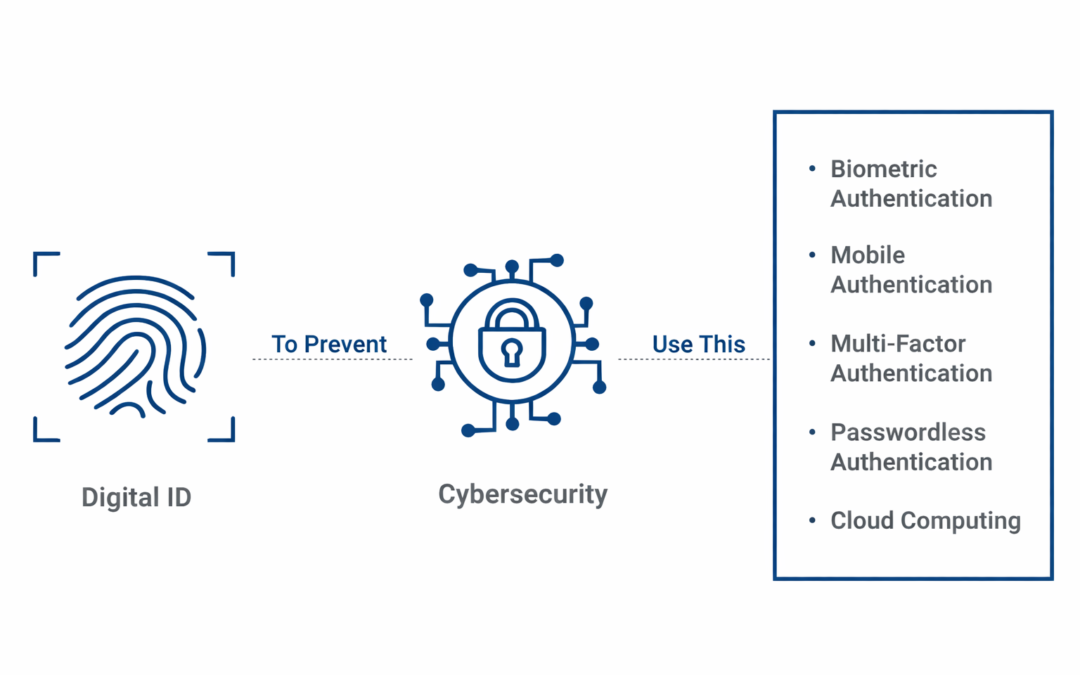
Dear Readers, Digital identities have become a critical component of cyber security in today’s digital age. Digital identity is the gateway to accessing a large number of internet services, such as financial transfers, societal media, healthcare and more, as people’s...

by Ciright | Jan 23, 2026 | Blogs
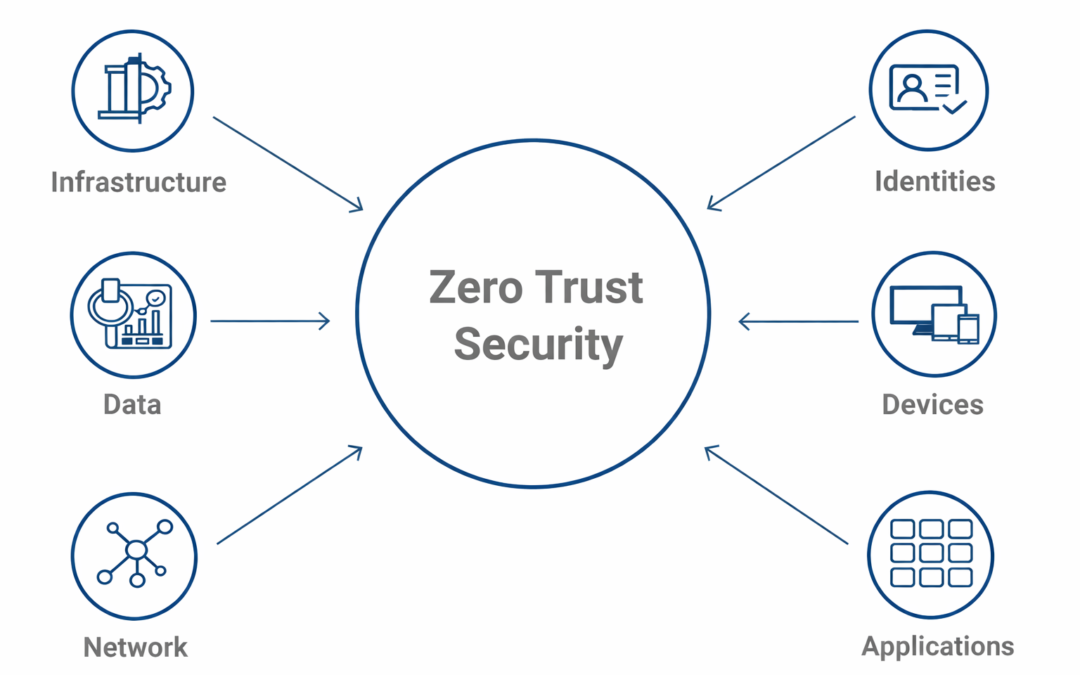
Dear Readers, Today’s cybersecurity environment does not support a perimeter-based security approach. The traditional approach of protecting your organization’s network from outside threats using firewalls and access restrictions is no longer enough due to the threat...

by Ciright | Jan 23, 2026 | Blogs
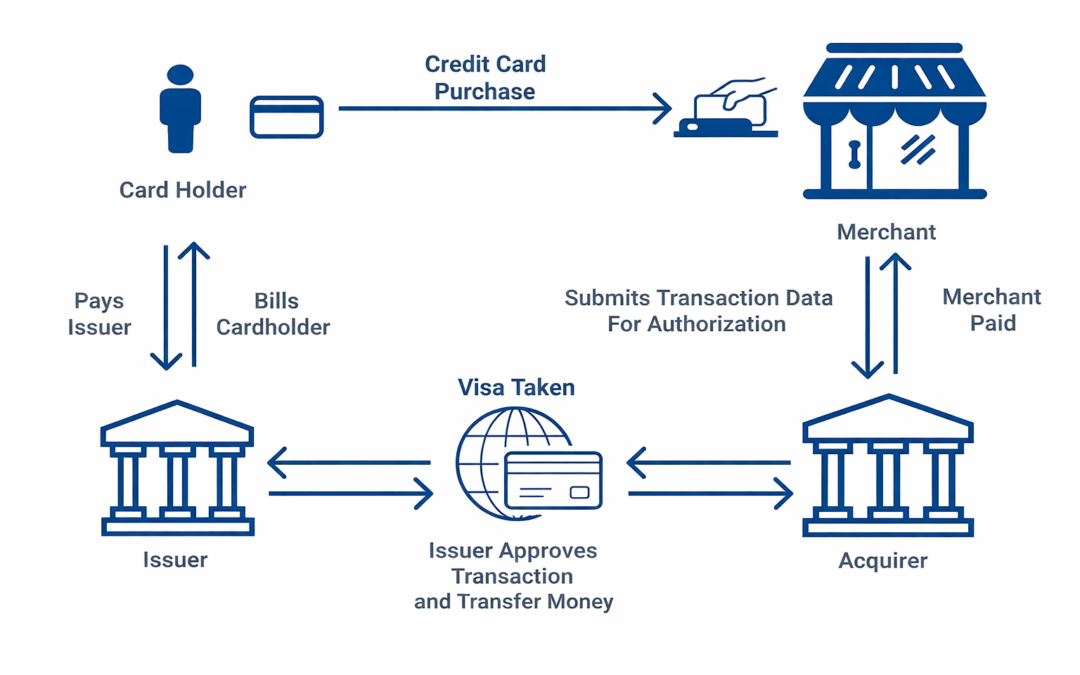
Dear Readers, In this blog we are going to learn about, Navigating the intricate world of payment processing involves understanding a web of players, each with unique roles and revenue-generating mechanisms. At the center are card networks like Visa, MasterCard,...

by Ciright | Jan 22, 2026 | Blogs
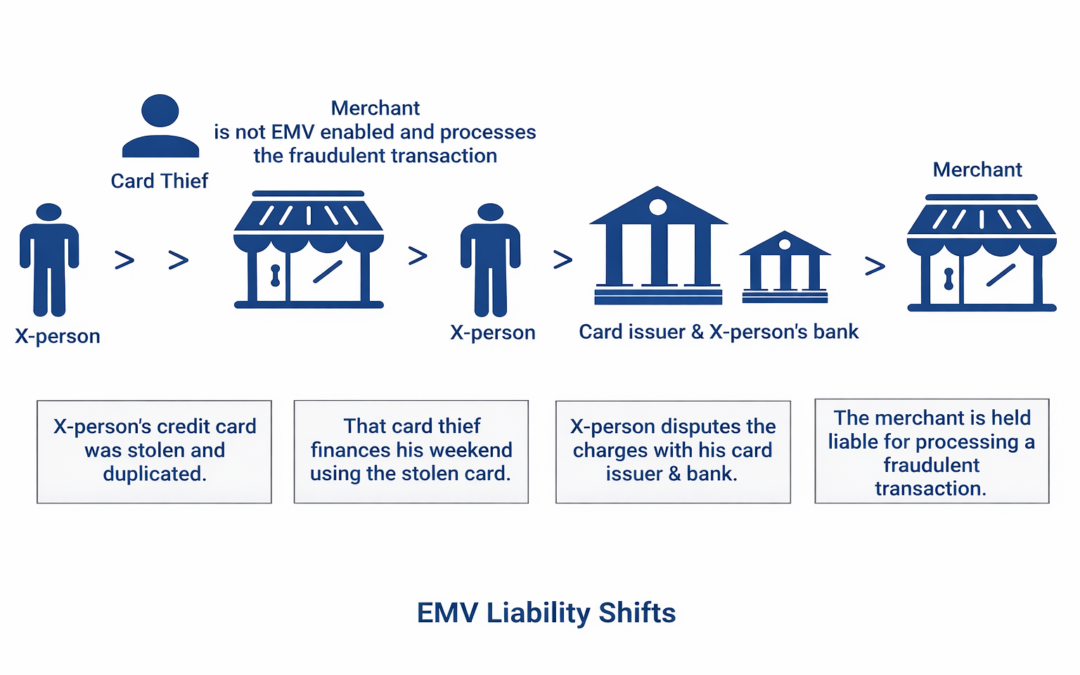
Dear Readers, How to navigate the EMV liability shift What you need to know about the EMV liability shift October 2015 marked the beginning of a new era for accepting payment cards in the US. That’s when the EMV liability shift took place, reassigning responsibility...



Recent Comments