
by Ciright | Jan 23, 2026 | Blogs
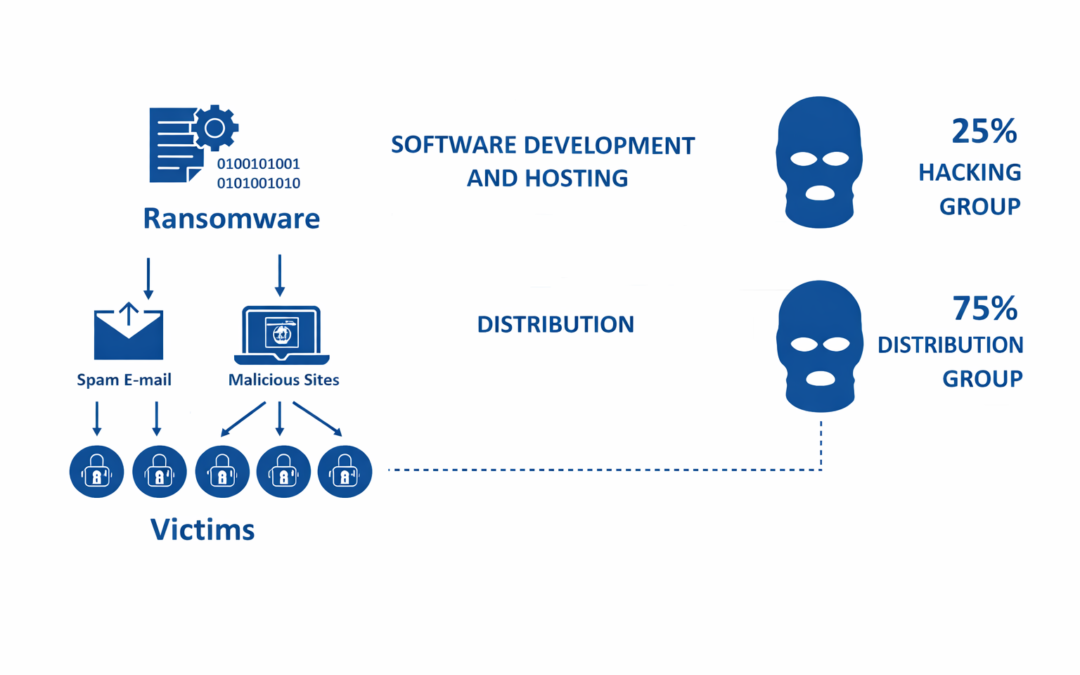
Dear Readers, This week’s blog is about how cybercrime is an ongoing threat for organizations, with incidents such as ransomware attacks, fraudulent sign-in attempts, and breaches due to stolen credentials continuing to rise. And no organization is safe –...

by Ciright | Jan 23, 2026 | Blogs
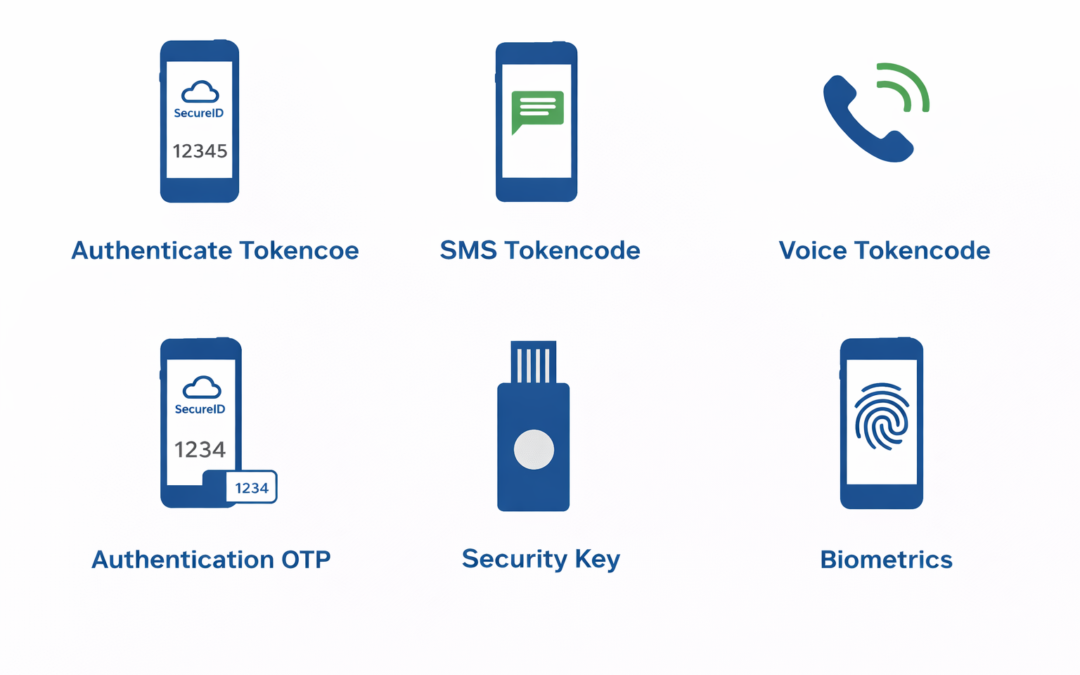
Dear Readers, This week’s blog is about how the cost of passwords is seen as a necessary evil. However, they present too many risks to ignore. For starters, passwords are too easy to steal and guess. The 2021 Verizon Data Breach Investigations Report confirms this,...

by Ciright | Jan 23, 2026 | Blogs
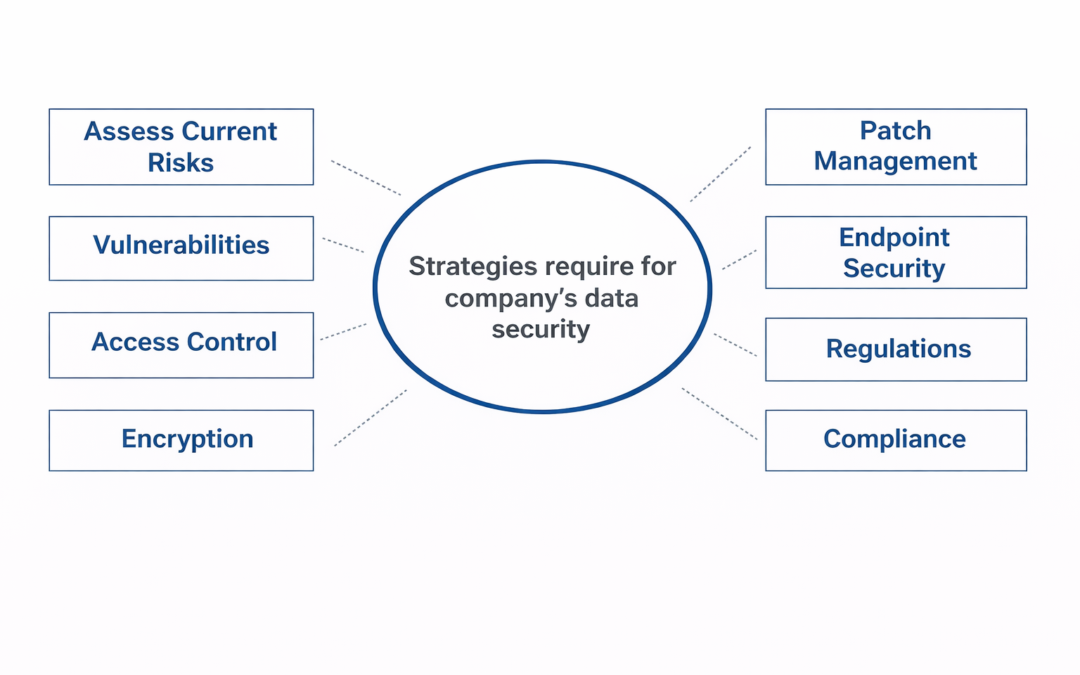
Dear Readers, A robust data security plan is an essential component of any company’s overall IT security strategy. A well-planned strategy may help prevent threats like cyber attacks, data breaches, and other types of security difficulties. We will look at some of the...
![RSA [Cryptosystem]](data:image/gif;base64,R0lGODlhAQABAAAAACH5BAEKAAEALAAAAAABAAEAAAICTAEAOw==)
by Ciright | Jan 23, 2026 | Blogs
Dear Readers, In this blog we are going to learn about, The RSA algorithm, a cornerstone of modern asymmetric cryptography, operates on the principles of using two distinct keys: a Public Key, which is shared openly, and a Private Key, which is closely guarded. In...

by Ciright | Jan 23, 2026 | Blogs
Executive Summary This white paper provides best practices for secure over-the-air (OTA) updates and patch management in IoT ecosystems. With 3,000+ devices in smart city deployments, maintaining trust in firmware and ensuring timely patch rollouts is essential....

by Ciright | Jan 23, 2026 | Blogs
Dear Readers, This week’s blog is about the passwords are seen as a necessary evil. However, they present too many risks to ignore. For starters, passwords are too easy to steal and guess. Passwords also require ongoing management from both users and IT staff. For the...


![RSA [Cryptosystem]](https://ciright.com/wp-content/uploads/2026/01/RSA-Cryptosystem-1080x675.png)


Recent Comments