
by Ciright | Jan 23, 2026 | Blogs
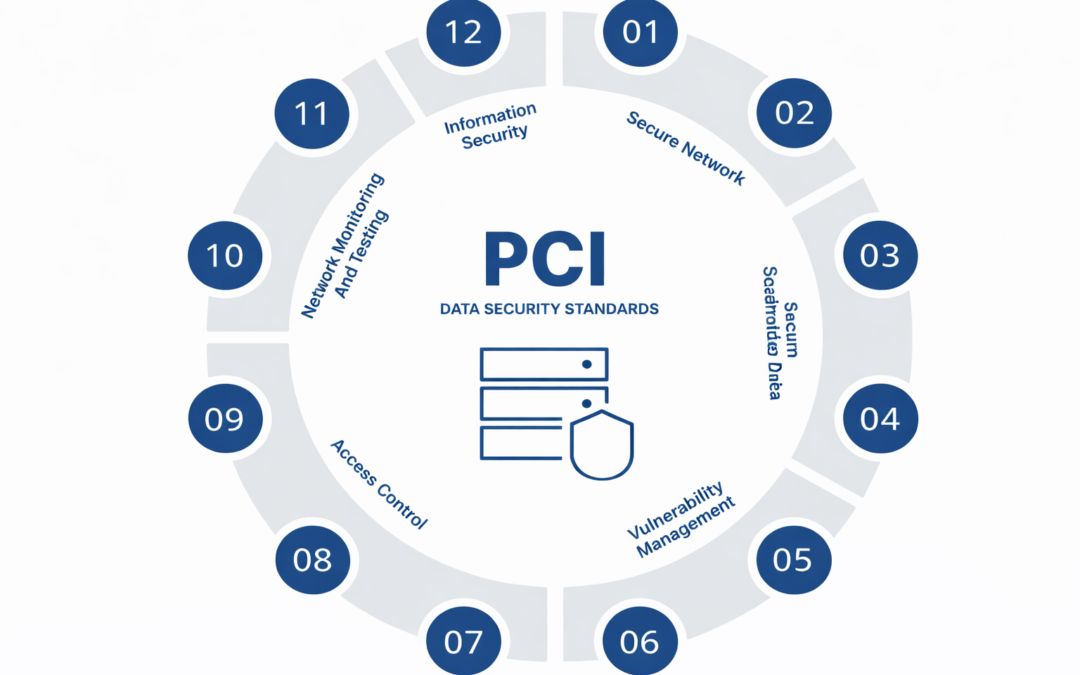
Dear Readers, The PCI Security Standards Council (PCI SSC) is a global forum that brings together payments industry stakeholders to develop and drive adoption of data security standards and resources for safe payments worldwide. PCI Security Standards are developed...

by Ciright | Jan 23, 2026 | Blogs
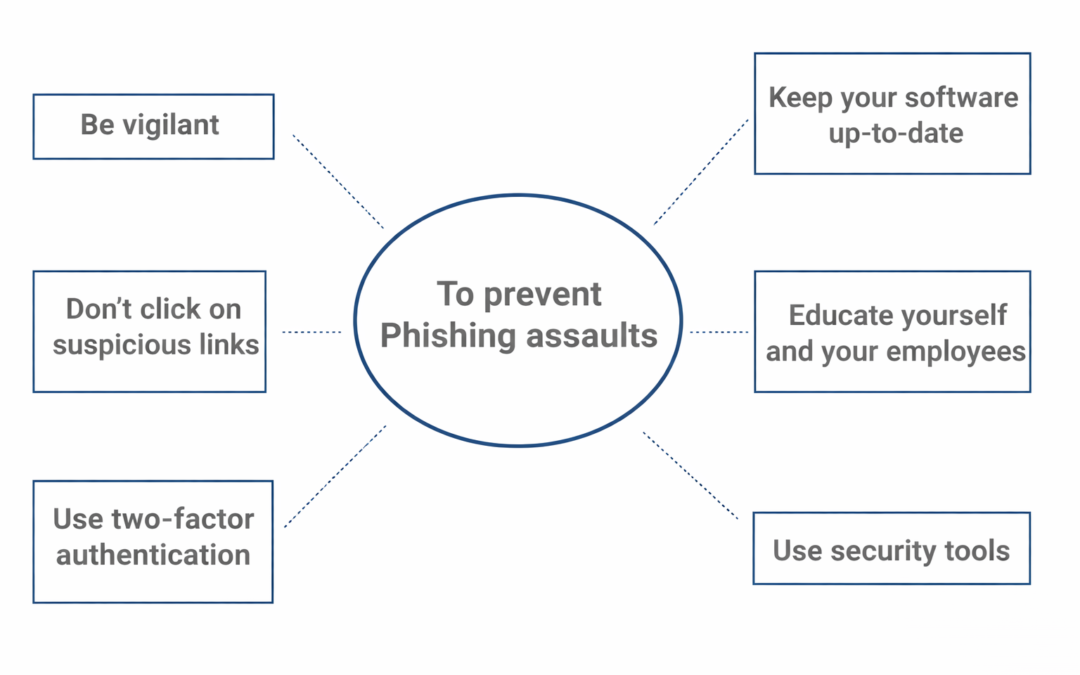
Dear Readers, Cyber assaults have grown in popularity and complexity in recent years, with phishing being one of the most prominent ways used by hackers to get access to critical information. Phishing attacks include sending phoney emails or messages that look...

by Ciright | Jan 23, 2026 | Blogs
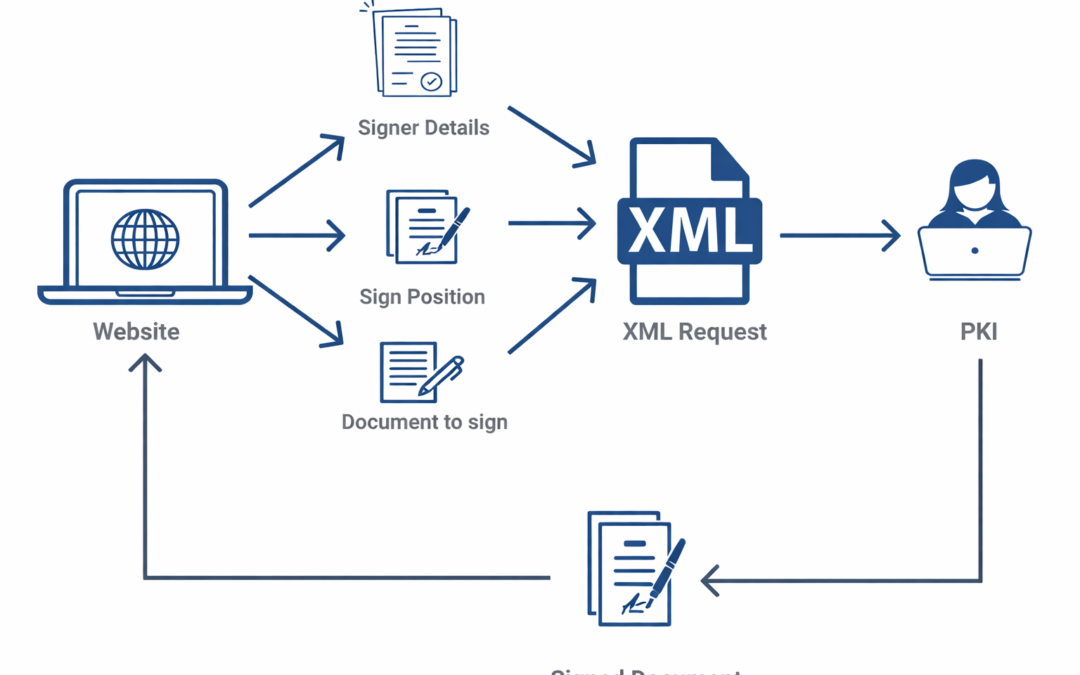
Dear Readers, In this blog, we will learn about Public key Infrastructure (PKI), Capabilities, Design, what it PKI consists of, Etc. but before that let’s understand the meaning of PKI. A public key infrastructure (PKI) is a set of roles, policies,...

by Ciright | Jan 23, 2026 | Blogs
Dear Readers, This week’s blog is about the Implementation, Best Practices, and Benefits of multi-factor authentication for Protecting Intellectual Property. Cybercrime is an ongoing threat for organizations, with incidents such as ransomware attacks, fraudulent...

by Ciright | Jan 23, 2026 | Blogs
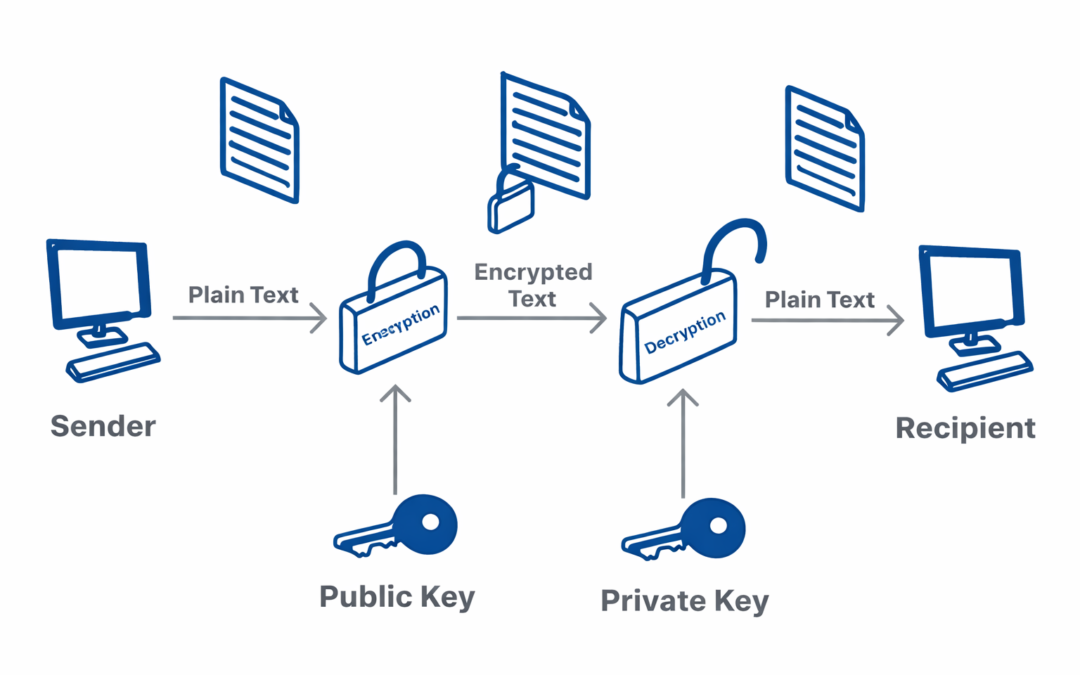
Dear Readers, In this blog we will learn about Uses of Public Key Cryptography, Applications, Hybrid Cryptosystems, Weaknesses, Algorithms, Alteration of Public Keys, Public Key Infrastructure & many more, but before that let’s understand...

by Ciright | Jan 23, 2026 | Blogs
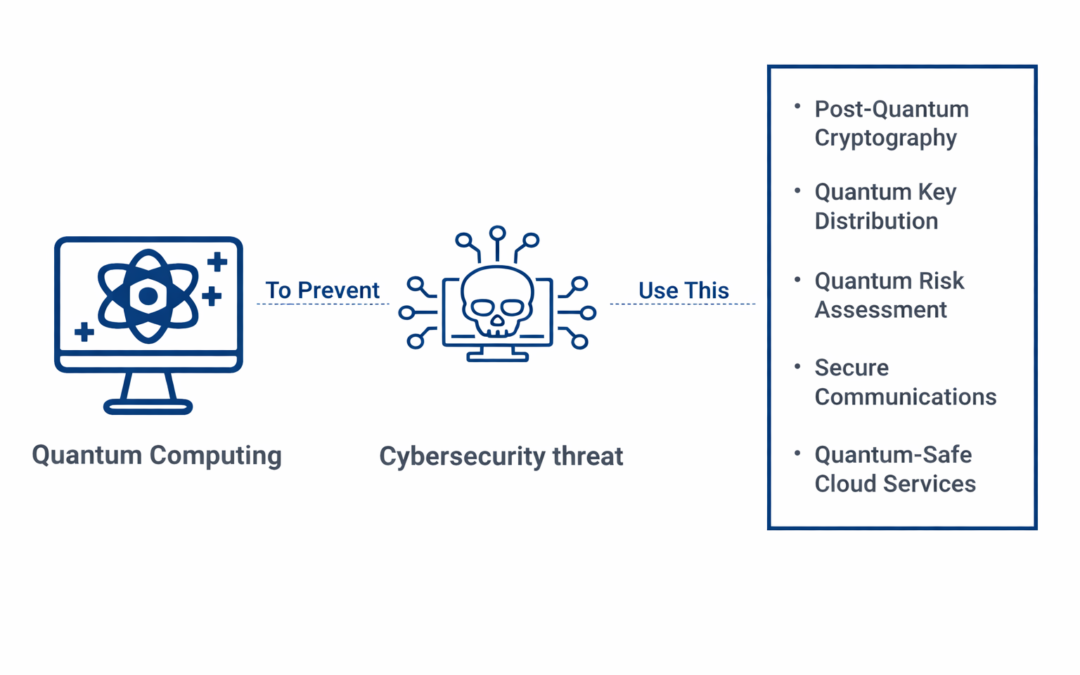
Dear Readers, Quantum computing is the most modern and revolutionary data processing approach. But, the benefits come at a cost: increasing cybersecurity risks. This essay will explain what quantum computing is, what security risks it may pose, and how you might...


Recent Comments