
by Ciright | Jan 23, 2026 | Blogs
Dear Readers, IP Ratings (Ingress Protection) A two-digit number established by the International Electro Technical Commission, is used to provide an Ingress Protection rating to a piece of electronic equipment or to an enclosure for electronic equipment.The...
![.ipa [File Format]](data:image/gif;base64,R0lGODlhAQABAAAAACH5BAEKAAEALAAAAAABAAEAAAICTAEAOw==)
by Ciright | Jan 23, 2026 | Blogs
Dear Reader, An .ipa file is an iOS and iPadOS application archive file which stores an iOS/iPadOS app. Each .ipa file includes a binary and can only be installed on an iOS, iPadOS, or ARM-based macOS device. Files with the .ipa extension can be uncompressed by...

by Ciright | Jan 23, 2026 | Blogs
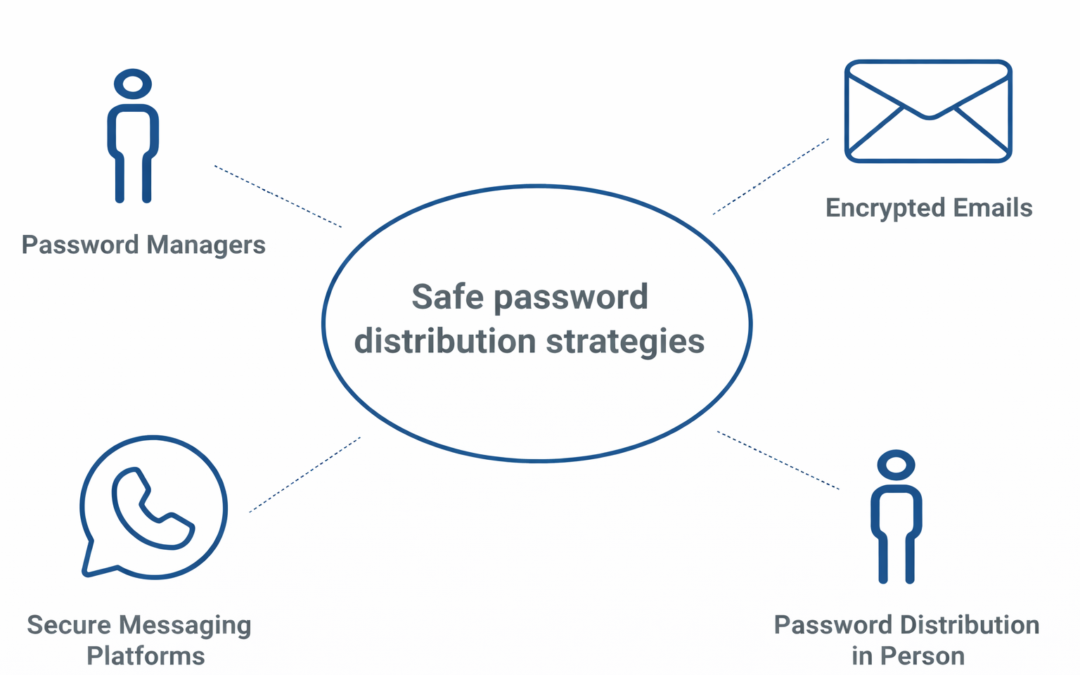
Dear Readers, Passwords are an integral component of our everyday life in the digital era. Passwords are the first line of protection against illegal access to our sensitive information, whether they are used to access our email accounts, online banking, or...
![.jar [File Format]](data:image/gif;base64,R0lGODlhAQABAAAAACH5BAEKAAEALAAAAAABAAEAAAICTAEAOw==)
by Ciright | Jan 23, 2026 | Blogs
Dear Readers, A JAR (“Java archive”) file is a package file format typically used to aggregate many Java class files and associated metadata and resources (text, images, etc.) into one file for distribution.[4] JAR files are archive files that include a Java-specific...

by Ciright | Jan 23, 2026 | Blogs
Dear Readers, What is a public key? In cryptography, a public key is a large numerical value that is used to encrypt data. The key can be generated by a software program, but more often, it is provided by a trusted, designated authority and made available to...

by Ciright | Jan 23, 2026 | Blogs
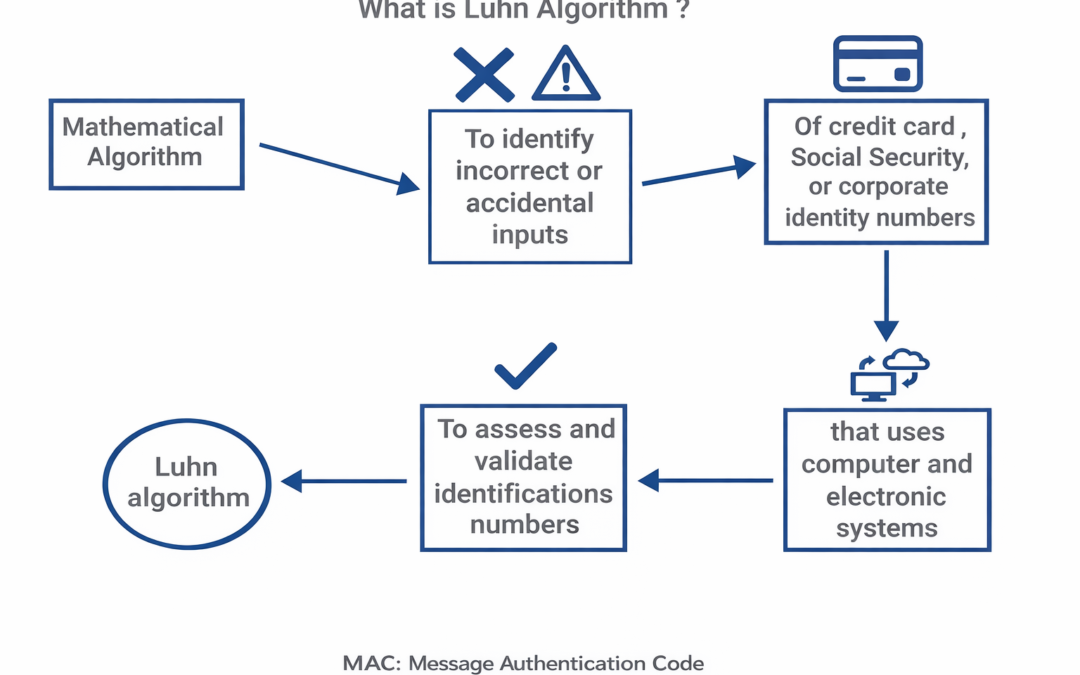
Dear Readers, The Luhn algorithm or Luhn formula, also known as the “modulus 10″ or “mod 10” algorithm, named after its creator, IBM scientist Hans Peter Luhn, is a simple checksum formula used to validate a variety of...


![.ipa [File Format]](https://ciright.com/wp-content/uploads/2026/01/ipa-File-Format-1080x675.png)
![.jar [File Format]](https://ciright.com/wp-content/uploads/2026/01/jar-File-Format-1080x675.png)


Recent Comments