
by Ciright | Jan 23, 2026 | Blogs
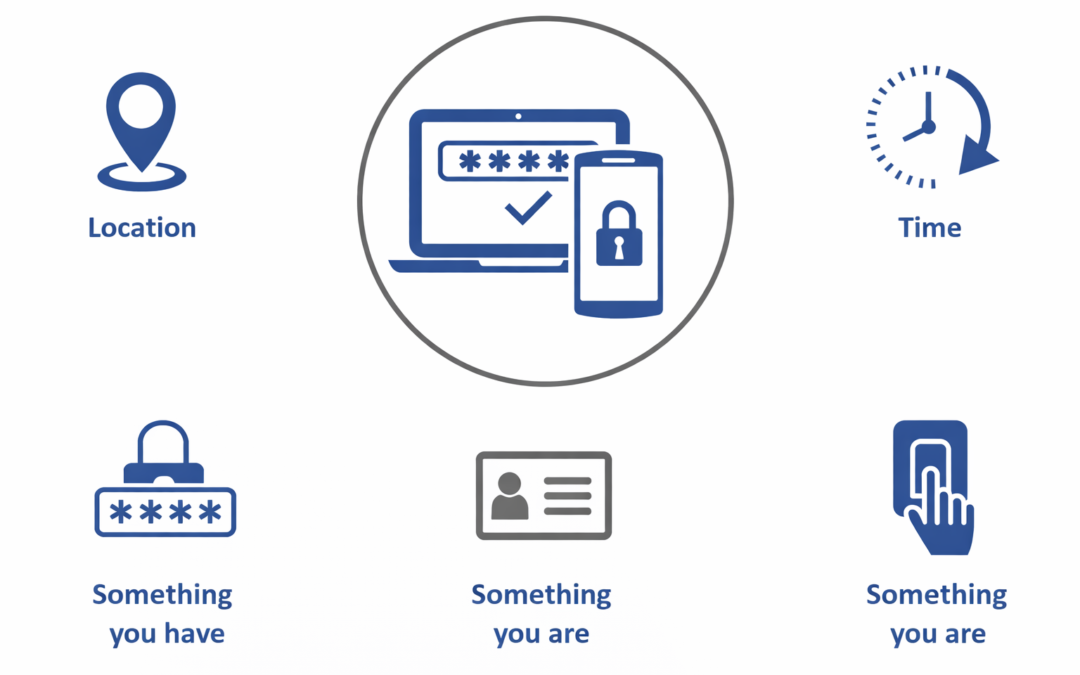
Dear Readers, This week’s blog is about the Implementation, Best Practices, and Benefits of multi-factor authentication for organizations. Companies are developing or reinvigorating their cybersecurity risk management programs; it’s vital to remember that...

by Ciright | Jan 23, 2026 | Blogs
Dear Readers, Coverage Chart United States CanadaDrivers License Machine Readable Technologies for U.S. Jurisdictions (June2019) JurisdictionMagnetic Stripe2D BarcodeRadio FrequencyNotesAlabama YesYes Mag Added June...

by Ciright | Jan 23, 2026 | Blogs
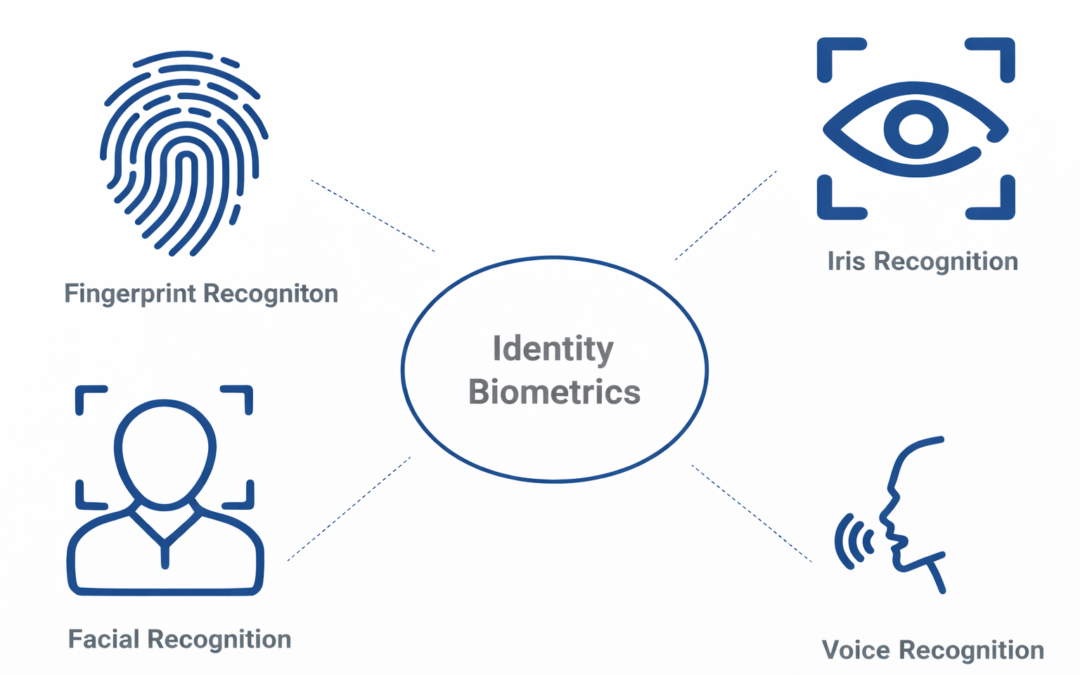
Dear Readers, For good cause, biometric authentication has grown in popularity as a means of identity verification. Biometric authentication, unlike traditional authentication methods such as passwords, relies on unique physical characteristics to verify an...

by Ciright | Jan 23, 2026 | Blogs
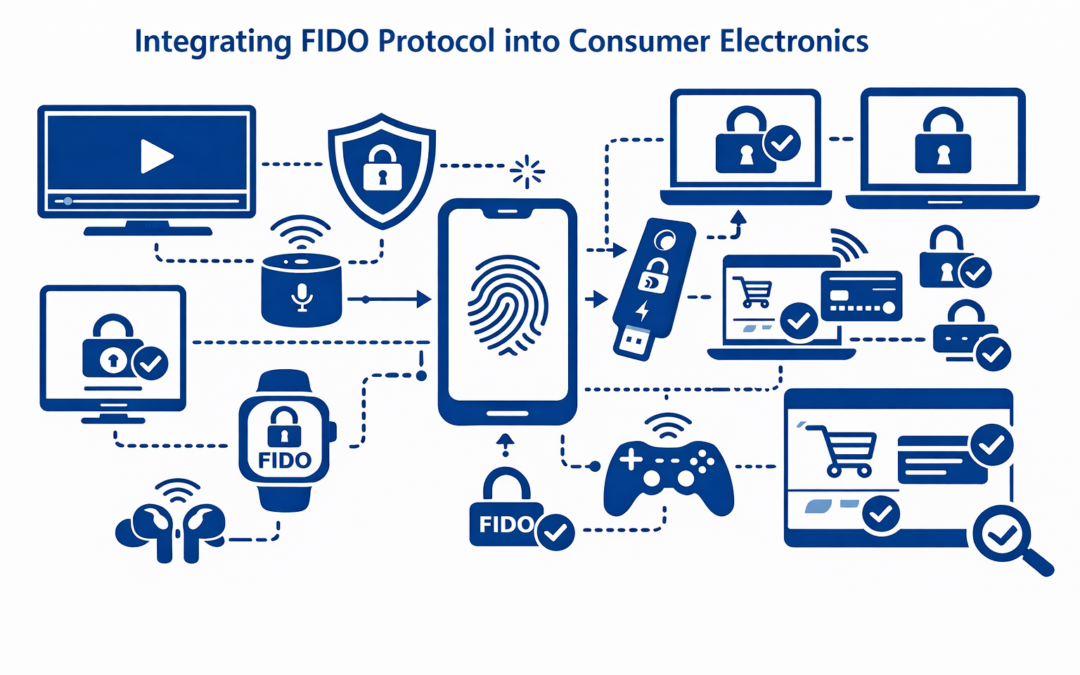
Executive Summary As cyber threats continue to grow in scale and sophistication, the need for stronger, phishing-resistant authentication mechanisms is more critical than ever. Ambimat Electronics, a leader in embedded hardware and secure microcontroller design,...

by Ciright | Jan 23, 2026 | Blogs
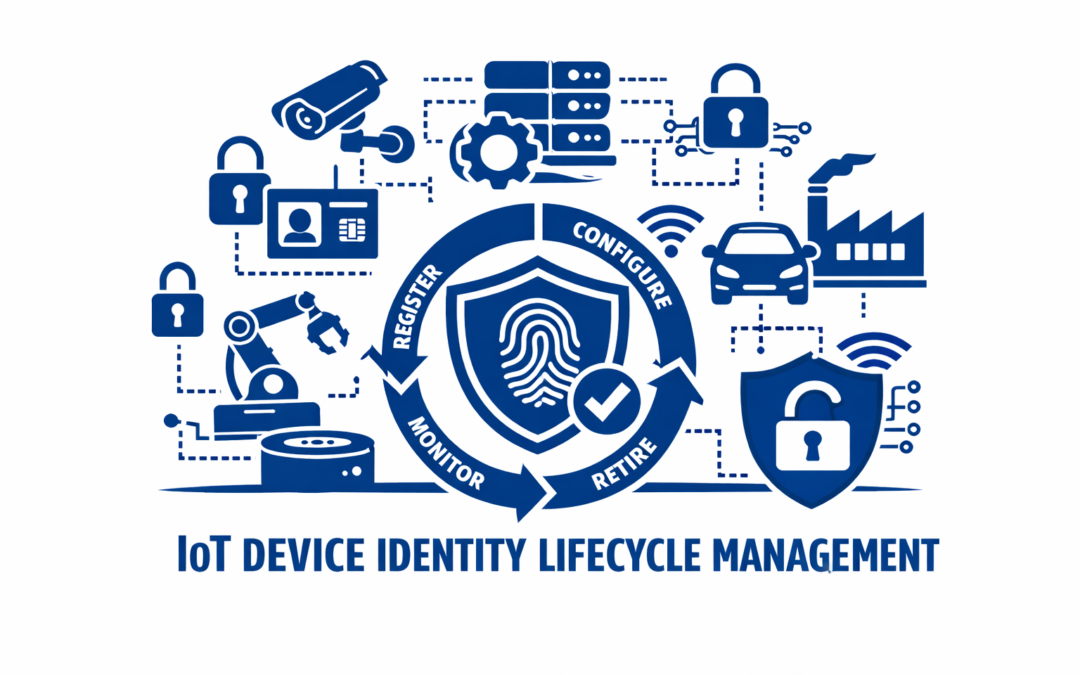
Executive Summary This white paper outlines best practices for IoT device identity and lifecycle management across smart city and industrial IoT deployments. From manufacturing to retirement, securing the identity of every device ensures trust, resilience,...

by Ciright | Jan 23, 2026 | Blogs
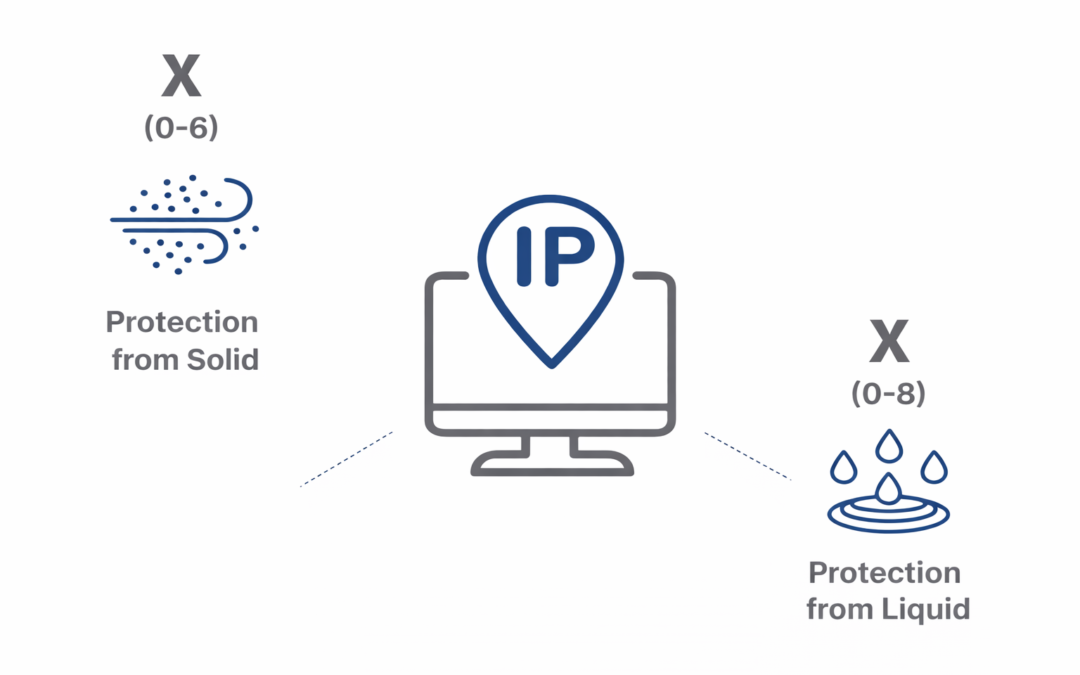
Dear Readers, The IP code or ingress protection code indicates how well a device is protected against water and dust. It is defined by the International Electrotechnical Commission (IEC) under the international standard IEC 60529 which classifies and provides a...


Recent Comments