
by Ciright | Jan 23, 2026 | Blogs
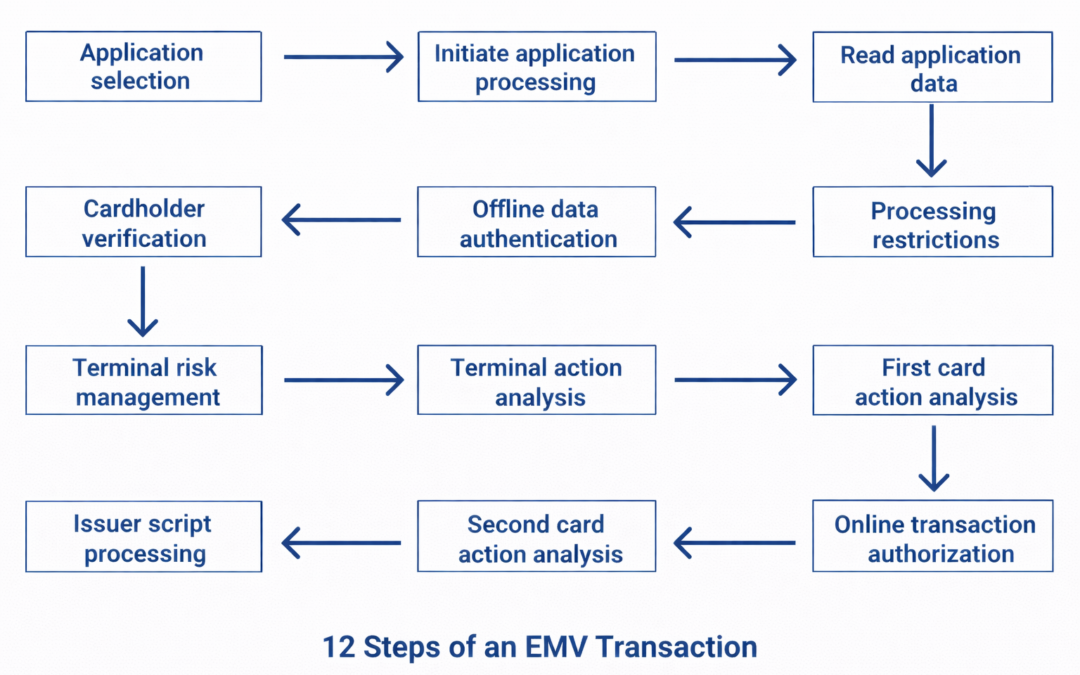
Dear Readers, There are 12 steps in an EMV transaction At most there are 12 steps in an EMV transaction. But some of these are optional or conditional. The best way to understand EMV is to think of a transaction as a conversation between the card and the terminal. The...

by Ciright | Jan 23, 2026 | Blogs
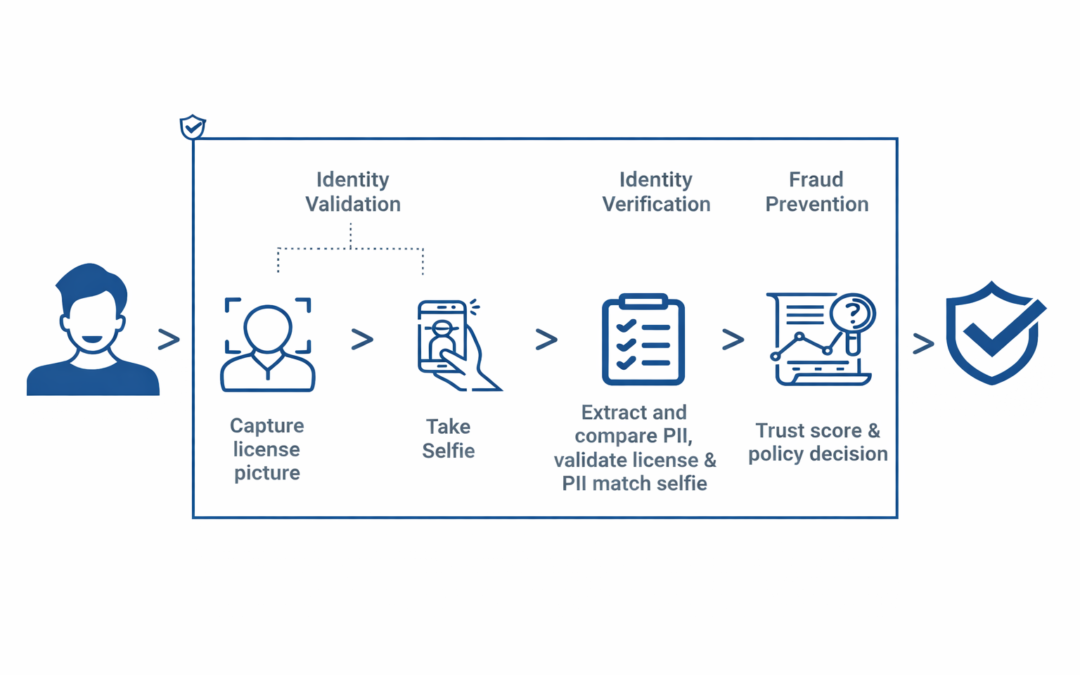
Dear Readers, Identity verification has become a crucial tool for many companies as the world gets more digital. Businesses must guarantee that they are working with real persons rather than fraudulent ones, from banking institutions to social media platforms. The...

by Ciright | Jan 23, 2026 | Blogs
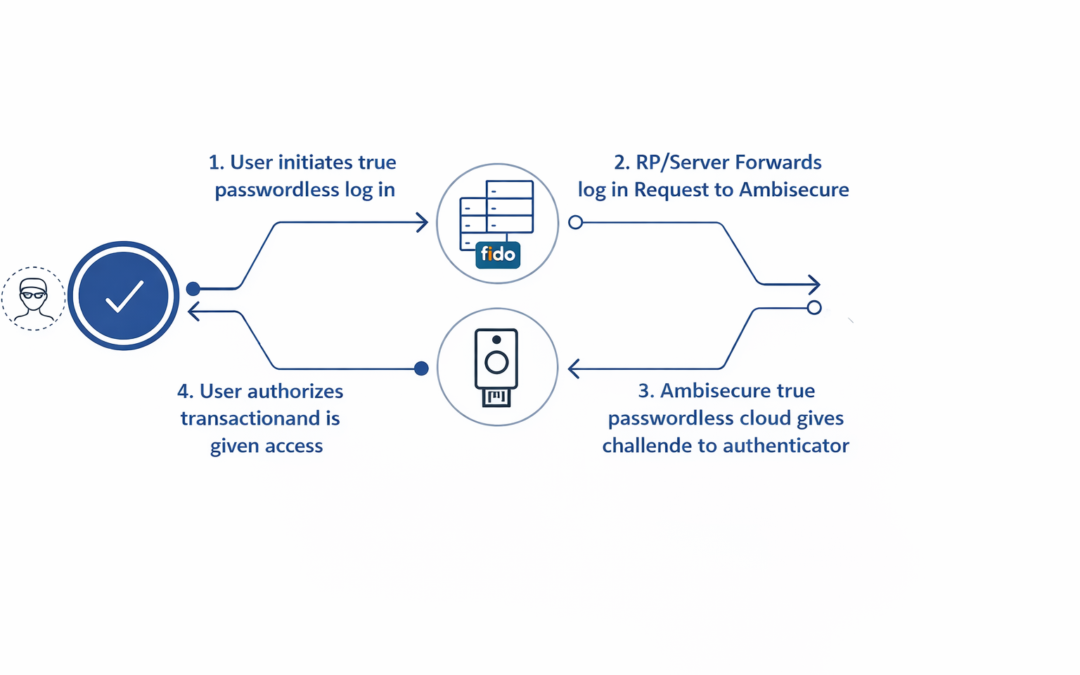
Dear Readers, The blog of this week is about a passwordless authentication system Through this blog, we aim to make our readers aware of passwordless authentication and how it has the potential to provide convenient access and strengthened security that today’s...

by Ciright | Jan 23, 2026 | Blogs
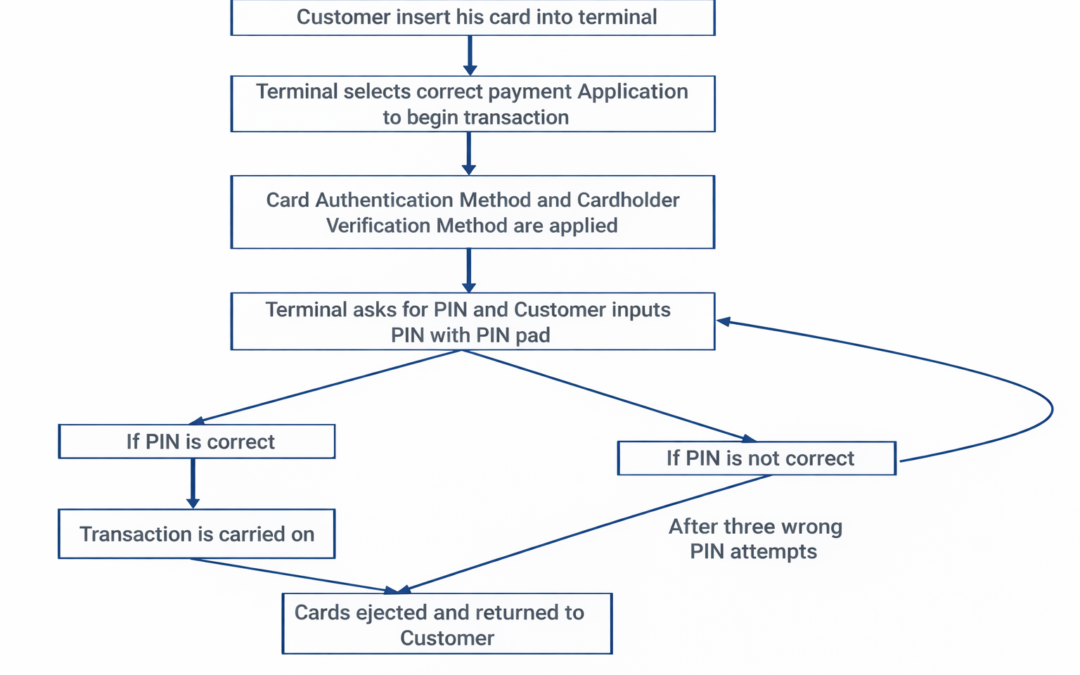
Dear Readers, Process DescriptionEMV StepsNMI’s Kernel ProcessCard detection and reset needs to be performed by the card interface functions specific to the hardware device being used. When a card is reset, it will respond with an Answer To Reset...

by Ciright | Jan 23, 2026 | Blogs
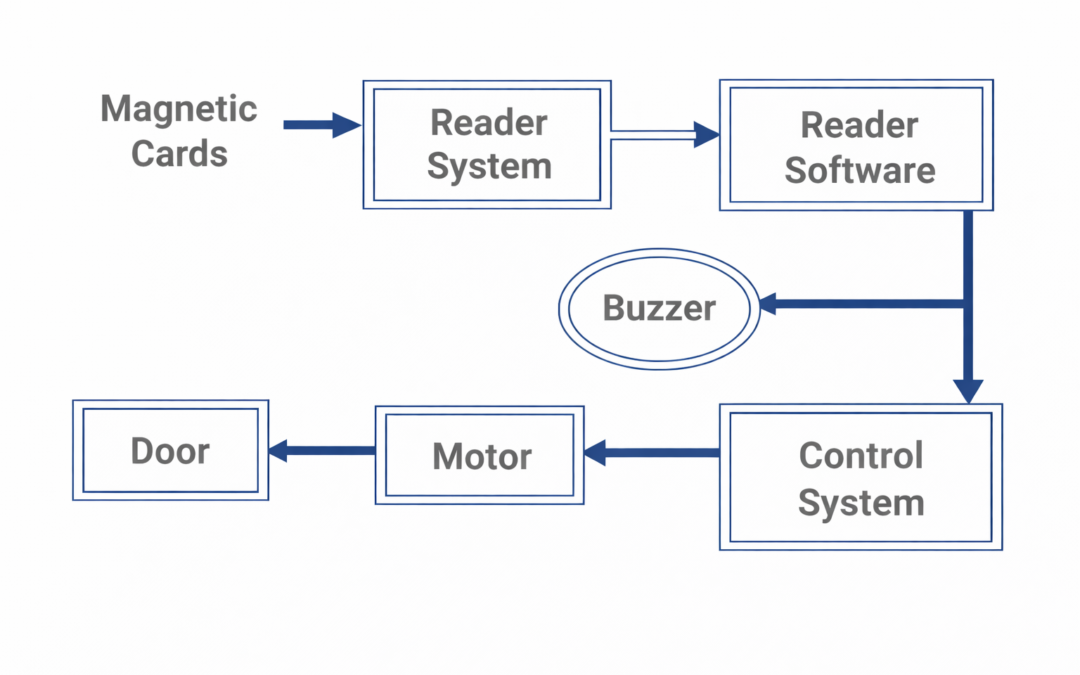
Dear Readers, A magnetic card is a rectangular plastic object (credit/debit card) that contains either a magnetic object embedded within the card or a magnetic stripe on the card’s exterior. A magnetic card can store any form of digital data. The electronic devices...

by Ciright | Jan 23, 2026 | Blogs
Dear Readers, One of the nice things about chip cards (ICCs) is that the data that comes out of them is virtually always supplied in a standard format, called BER-TLV. In plain English: Basic Encoding Rules, Tag-Length-Value (a quaint but informative article about it...



Recent Comments