
by Ciright | Jan 23, 2026 | Blogs
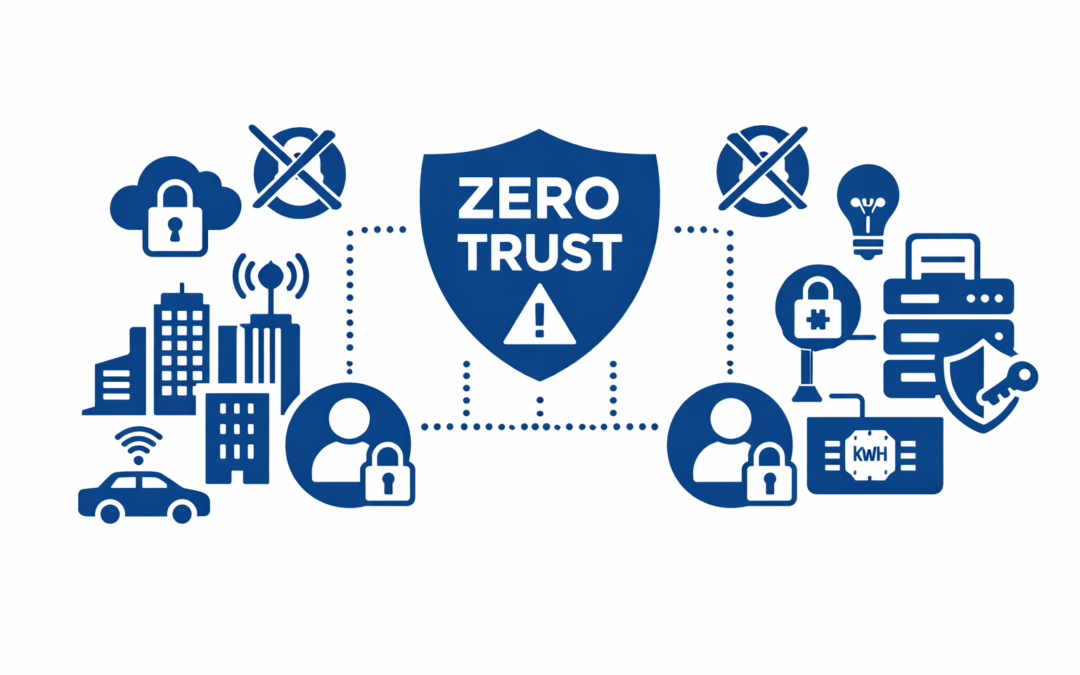
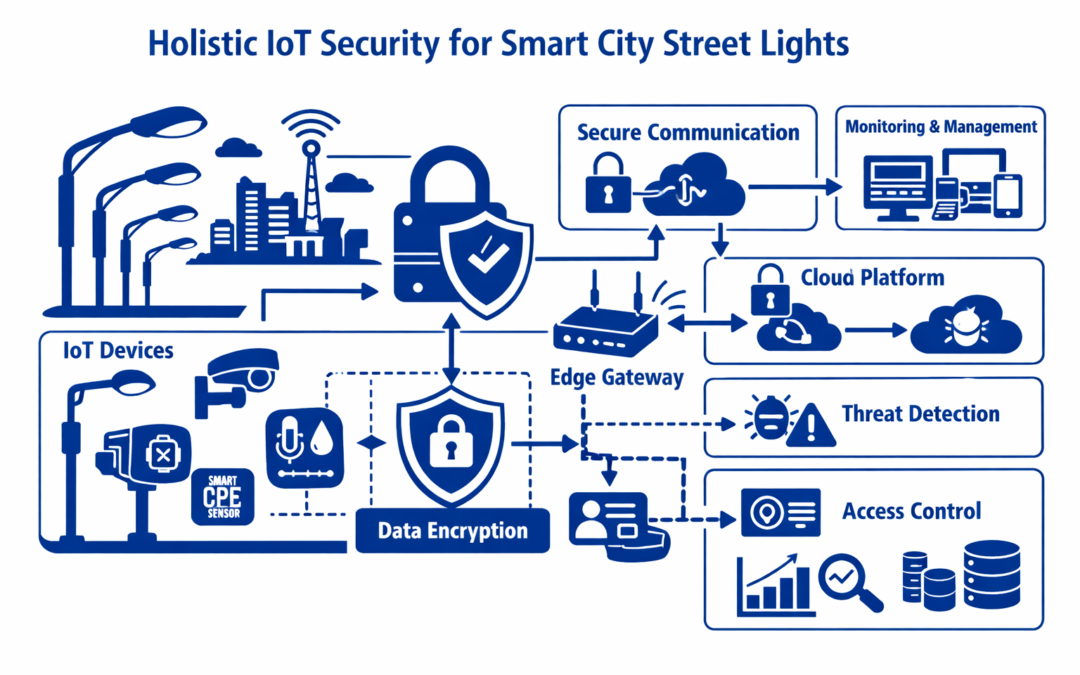
Executive Summary This white paper presents a comprehensive guide to implementing zero-trust security in smart city IoT deployments. With thousands of interconnected devices such as street-light controllers, gateways, and cloud platforms, the attack surface...

by Ciright | Jan 23, 2026 | Blogs
Dear Readers, In order to support the multiapplication business requirement, the terminal should implement appropriate procedures for card application selection. To this end the acquirer that manages the terminal shall maintain a list of the card applications...

by Ciright | Jan 23, 2026 | Blogs
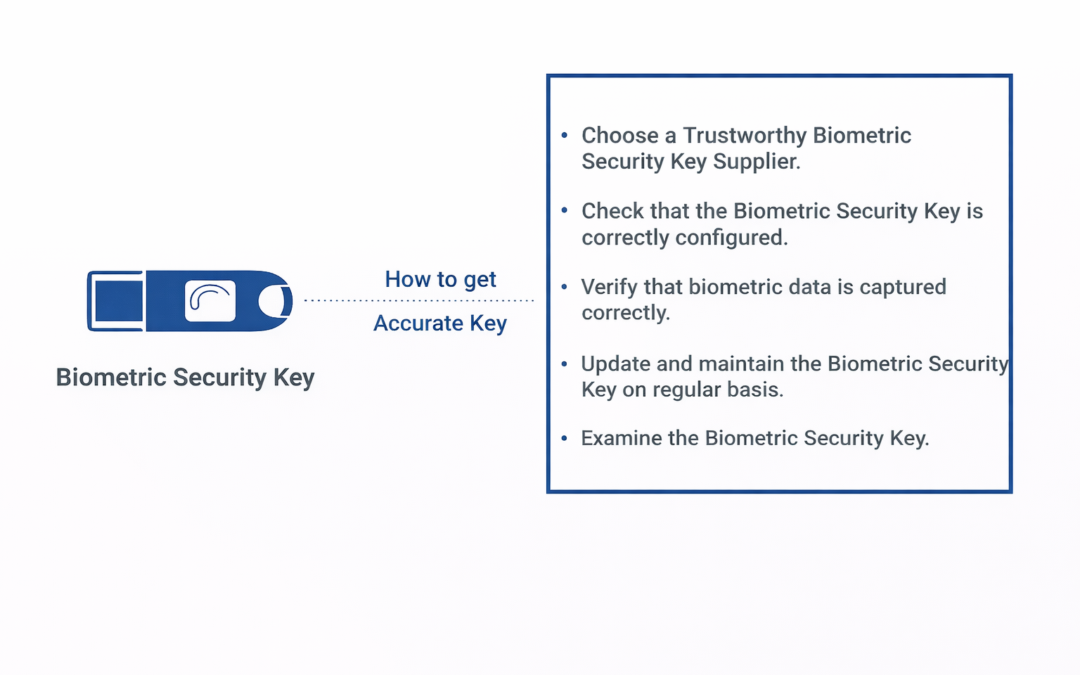
Dear Readers, Passwords have shown to be untrustworthy for safeguarding our internet accounts in today’s digital world. As a result, biometric security keys are becoming increasingly popular as a more secure alternative to standard passwords. To validate user...

by Ciright | Jan 23, 2026 | Blogs
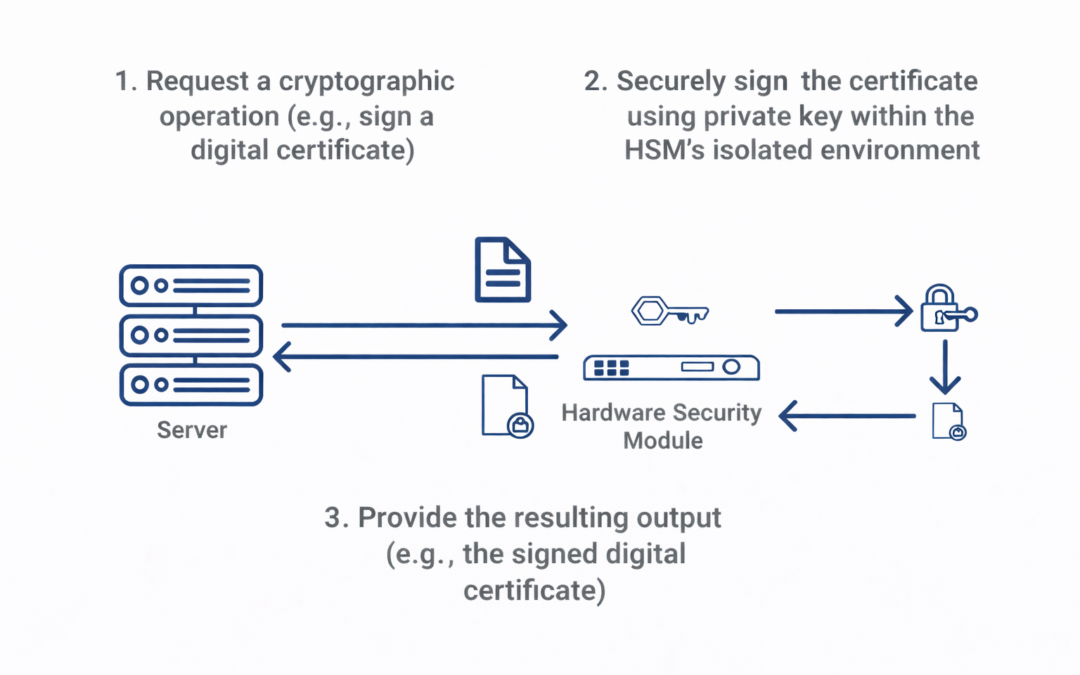
Dear Readers, What is a Hardware Security Module (HSM)? Hardware security modules (HSMs) are hardened, tamper-resistant hardware devices that secure cryptographic processes by generating, protecting, and managing keys used for encrypting and decrypting data and...

by Ciright | Jan 23, 2026 | Blogs
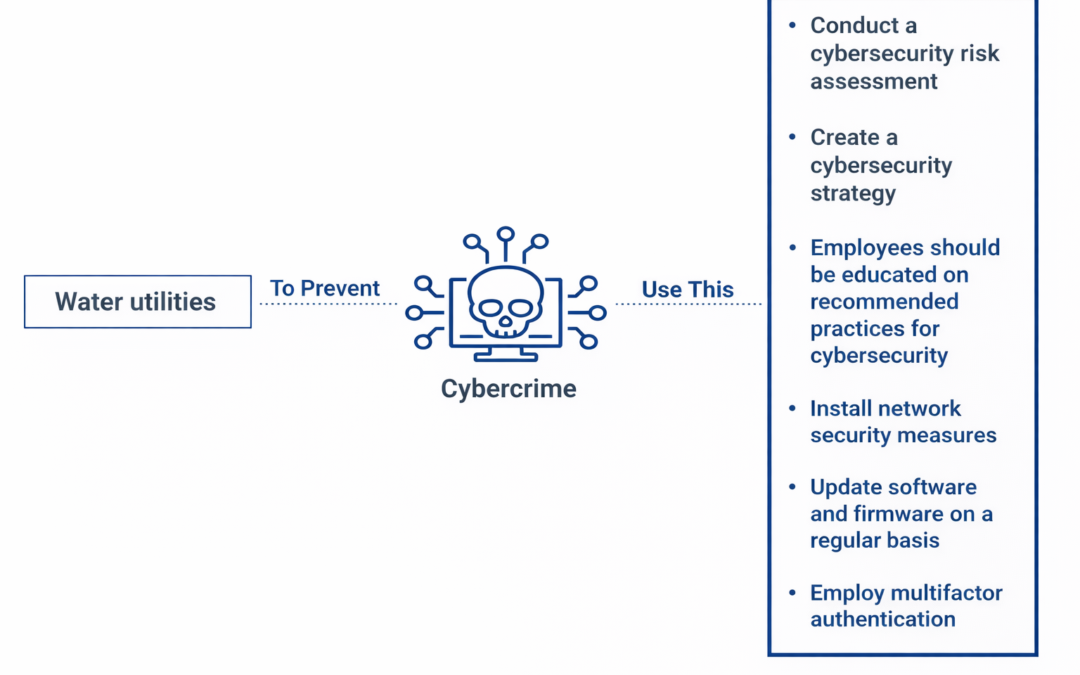
Dear Readers, Water utilities are vital community services that supply safe drinking water and wastewater treatment. They are, nevertheless, vulnerable to cybercrime, just like any other essential infrastructure. Hackers might compromise the water utility’s network...



Recent Comments